Picexa Viewer is a program that can be downloaded from its own website or some of the free download sites found online. It is touted as being an image viewer that delivers fast results. But, the company behind this, Taiwan Shui Mu Chih Ching Technology Limited has a reputation for delivering suspect applications in the wild. Some of them include WinZipper, Qone8.com and Omiga Plus.
This program may cause ads to appear on your machine. Even though it is not malware itself, it can still open you up to other issues. It can cause system issues, and redirect you to sites that can be problematic.
Also, the program is frequently bundled with other free software that may seem legitimate. Pay careful attention whenever installing free software because you may be getting more than you bargained for.
PicExa can be removed manually or automatically. Automatically is the preferred method because it is easier to do and it takes less work to complete. In order to perform the automatic installation, it is recommended that you use a program like SpyWare Hunter or a similar program. If you would like to try out SpyHunter, you can use the link below to complete the installation.
It is most likely that you got the PicAxa virus due to it being bundled with another program. That is why it is important to be careful whenever you install programs from free software websites. If you do insist on using free software websites, then you should be very careful when doing the installation. Try to always do the custom installation. This will give you the option to unselect all the extra programs that are being installed. And, it will give you the option to unselect the PicAxa application. If you do the custom installation, pay close attention to the installation and make sure you are selecting the correct option to deny the installation of the extra program.
How To Remove PicAxa
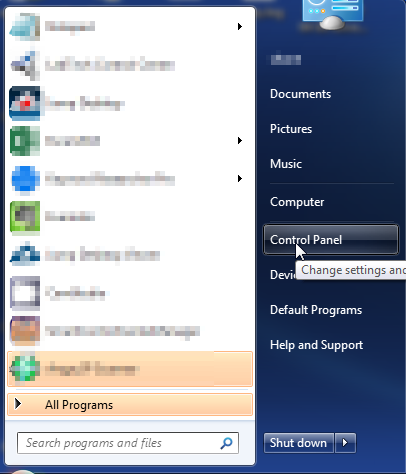
- Open up control panel by clicking on the start button in the lower left corner of your computer, and then going to Control Panel
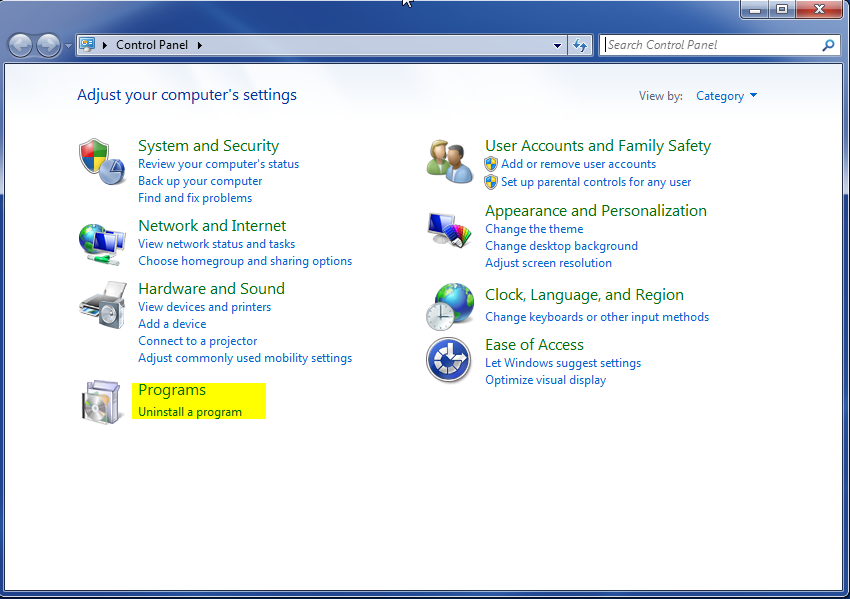
- Once, you are in Control Panel, go to the link labeled “Uninstall a Program”. If your computer does not look like the view below, you may have to sort by categories at the top right.
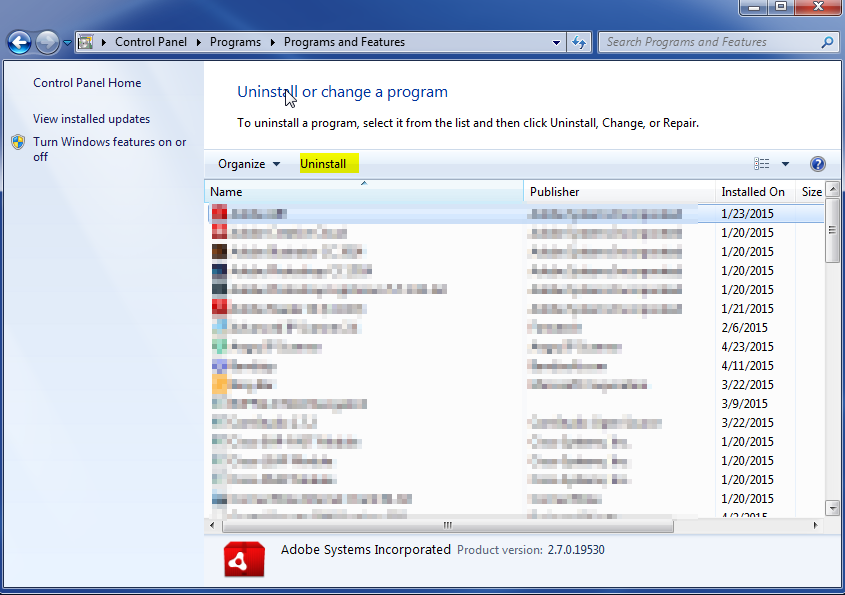
- Once in the uninstall programs section, look for the offending program. You can scroll by date installed to find programs that were installed recently. This may be a clue as to what the offending program is. Once you have found the program, highlight it and select “Uninstall” to remove
Once you have done this, you will need to go into your browser and set it to its default settings to remove the other changes it made. You will also want to scan your computer to make sure no new issues were introduced by the vulnerability. A good tool to use for this is MalwareBytes. If you already have a virus scanner, you should run this as well.
