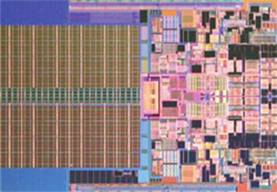
The Penryn CPU is another in Intel's line of Core 2 processors and the first fabricated using its 45nm die technology. The processors replace the 'Merom' range of processors, the and dual- and quad-core versions catering for the differing requirements of consumer machines. The Penryn is … [Read more...]
Guide to the Intel Core 2 Quad and Extreme processors
In November 2006 Intel released the first in their range of Intel Core 2 Quad processors. Codenamed the 'Kentsfield', the newly released processors were two Core 2 Duo chips connected by a 1066 MHz FSB all continued on one multi-chip module. The series number for the more powerful Core 2 … [Read more...]
Intel Mobile Pentium II technology guide
The natural progression of the low-power Deschutes family of Pentium II processors to the portable PC market took place with the launch of the Mobile Pentium II range in April 1998. The new processor, and its companion Mobile 440BX chipset, … [Read more...]