RotaryTuners is another malware/spyware application that causes annoying commercial ads and popups inside your browser. If you are infected with this application, then you will want to take measures to remove Rotary Tuners as soon as possible.
It is typically bundled with software that promises to make your computer experience more productive. Basically, it aims to trick you into getting the application onto your system.
You will notice differences almost immediately after the application is installed. The third party ads will start showing in short order. The program work in all the popular browsers including Google Chrome, Mozilla Fierfox and Microsoft Internet Explorer. Even worse is that the ads are coming from servers that are known to serve up malicious ads on a continual basis.
Furthermore, some of the ads that are served use redirection and will send the user to malicious websites. This could cause further issues and increased infections on the computer.
Since the software is bundled with other applications deemed to be useful, it is a good idea to be careful where you download applications. Furthermore, always try to choose the manual installation when available. This will give you the option to skip any applications that could prove to be problematic.
We have included steps below to remove Rotary Ads manually. It is not very difficult. However, if you would like a more automated and simple way to remove the application then we recommend SpyHunter. This free program will scan your computer and alert you to any issues it finds.
Uninstall Rotary Turners from Windows.
- Open up control panel by clicking on the start button in the lower left corner of your computer, and then going to Control Panel
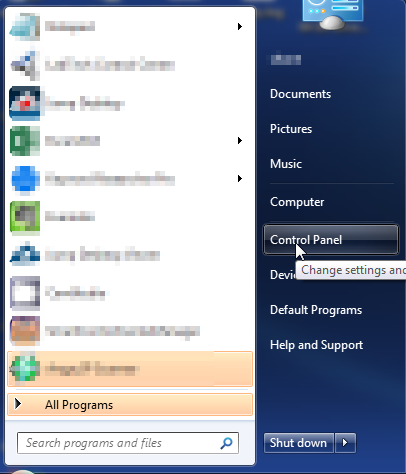
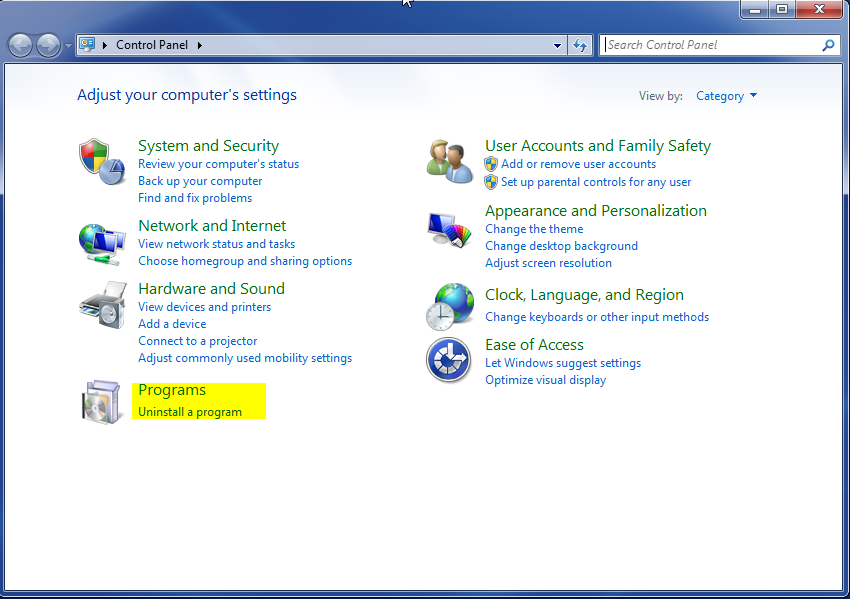
- Once, you are in Control Panel, go to the link labeled “Uninstall a Program”. If your computer does not look like the view below, you may have to sort by categories at the top right.
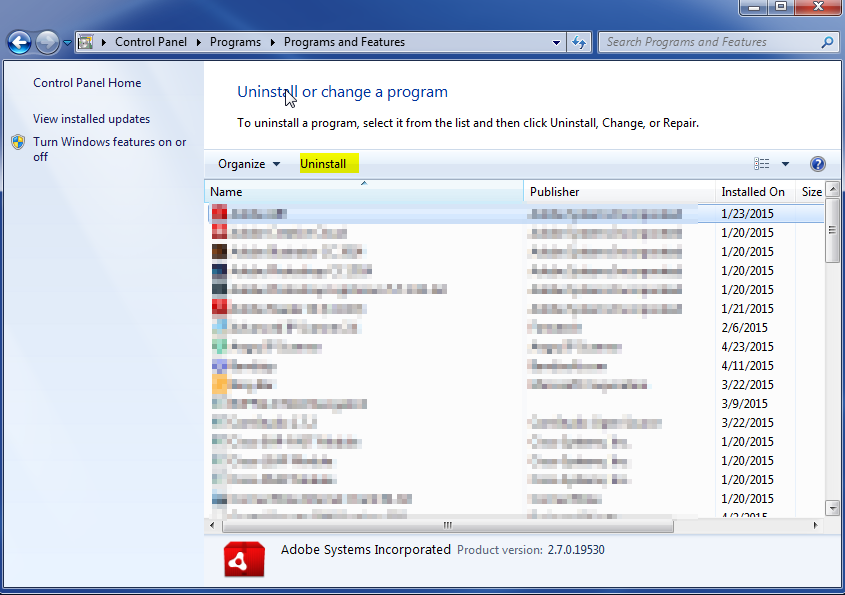
- Once in the uninstall programs section, look for the offending program. You can scroll by date installed to find programs that were installed recently. This may be a clue as to what the offending program is. Once you have found the program, highlight it and select “Uninstall” to remove
Once you have done this, you will need to go into your browser and set it to its default settings to remove the other changes it made. You will also want to scan your computer to make sure no new issues were introduced by the vulnerability. A good tool to use for this is MalwareBytes. If you already have a virus scanner, you should run this as well.
