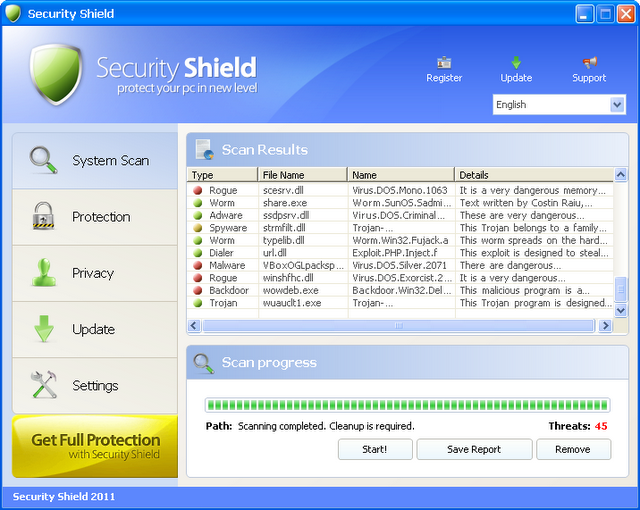
Security Shield 2011 other wise known as just Security Shield is a clone of the past Security Shield malware that came out in 2010. It’s also a clone of System Tool. System Tool is considered by many to be the most prevalent malware of 2010. The makers of the fake security client have upped their game making Security Solution 2011 even harder to remove
Download Security Shield Removal Software
Tested by PCTechGuide.com to Confirm it does fully remove Security Shield
Simplest Security Shield 2011 Removal Option
Hiring a pro to remove Security Solution 2011 is of course the simplest option, but it’s also the most expensive. However you have some very affordable options you may not be aware of. If you have your computer repaired online you can save a bundle and have your computer fixed right away instead of waiting a few days for a computer repair shop. We recommend a company based out of California. They are true experts when it comes to repairing computers remotely and can fully remove this virus as well. Check out this Remote Computer Repair solution
Visit: http://www.pcninja.com to chat live with a expert about your issue
Using Anti-Virus Clients to Remove Security Shield 2011
We tested Spyware Doctor with Antivirus against Security Shield 2011 and it fully removed all traces of this virus.
You may also want to check out our Anti-Virus Reviews page as well as our Internet Security Reviews page.
Manual Security Shield 2011 Removal
Here are the instructions we found that will help you remove this malware threat. Keep in mind the below traces will change and mutate over time.
Step 1. Stop the Security Shield 2011program from running and delete the file
To do this we need to locate were the .exe / executable file is and either re-name it or delete it if we are in safe mode and the program is not running. You can not delete a file while it is in use. So if you are in normal mode you will need to re-name the file first then re-boot your computer and after it starts back up you can delete the file.
Here are the known file location for Security Shield 2011
XP
- C:Documents and SettingsAll UsersApplication Data[random]
- New Path C:Documents and SettingsUSER NAMELocal SettingsApplication Data
Windows 7 / Windows Vista
- C:ProgramData[random characters ][random characters].exe
- New Path C:UsersUSER NAMEAppDataLocal
The name of the executable file will always be different. An example would be sdf1sd2fr1g.exe Normally the file name does not make any sense at all.
To aid in locating this threat you can sort files in the above folders by data modified. Chances are you only have a few files that were modified within the last few days and the Security Shield 2011 threat will be one of those. Often times it might even have the icon with the executable for easy identification.
Step 2. Run a full virus scan using Spyware Doctor with Antivirus to ensure you have no other viruses installed on your computer. If the scan comes up clean you are good to go. If not you can then manually delete any other traces that the client finds. Spyware Doctor with Antivirus can also assist you in removing this malware as well. Download it Here
If all else fails or you just need expert help right away we can’t recommend out this Computer Repair company enough. http://www.pcninja.com

This was an incredible help thank you so much. FYI people first start regularband you can find the file name by clicking on it’s tab, mine was cCrhdudududu.exe
best way to remove this software is to reboot your pc while pressing the f8 key, this will put your pc in safe mode, find the restore program and restore your pc to an earlier date, worked for me!
Thank you so much! You’ve just rescued me! Statha
u saved me too !!
bravo !!!
thanks a lots
saved me too, found the crap exactly as stated above: in C:Documents and SettingsUSER NAMELocal SettingsApplication Data
Btw: got it from the Orbitz site. Beware!
I am still trying to resolve it. But most likely I too got it from Orbitz site as I was searching for flight deals.
I am still trying to clean mine up! I got it from orbitz as well 🙁
I just got this virus from orbitz also. how to heck can they allow this?
I got it from Orbix too….wow
Orbitz was most likely where I got it too — I was searching for flights. I’m sticking to the airlines’ individual web sites from now on.
WOW! Pried my infected laptop out of Staples ‘tech”s paws after three days and $70, not yet fixed with at least another day and at least $80 to go… found this and fixed it in 15 minutes! Had this problem appear a year or more ago and was able to execute restore from desktop — this new virus version blocked restore from the desktop, blocked AVG antivirus, even blocked remote network access (‘msconfig’) for the AOL software tech and the Staples so-called ‘tech’. Reboot with F8, Restore, and I am back in business…THANKS! BTW, looks like anti-virus software does not catch this if you’re stupid enough to open a nasty link!
Thnx for your help!
THANK YOU!!!
I would say that is the easiest way, if you can’t or don’t want to do what the article says then definitely use restore!
yep. Restore is a great tool. However malware will often times disable it so it’s not a cure all
I got hit 2-3-2012 and I have virus protection. Could not execute anything on the internet, file manager, task manager – nothing at all without those pesky secure shield warnings. In WIndows 7 I found the restore program at system32.restui.exe and I only lost about 3 days – but my data files were ok! 5 minutes later I had a working PC. Thank you so much. Thank goodness I had my laptop from work at home so I could find your post!
Rock on! Glad we could help get you sorted
I was’nt concentrating, got caught, used Gkaufmann’s advice and am fine now , Thank you very much.
Davemason50…you the man! Thanks buddy 🙂
Glad we were able to help you out.
jerdei whats the best stuff to use……you mention microsoft essentials….if i down laod that oen and use AVG will that be ok.or is there some other ones better.hopefully free ones…………….
The best AV clients out there are all paid clients. The free AVG for instance offers no up front protection. It’s only after you get infected that it kicks. I do not like recommending out free products because it gives a false sense of protection. NO free client out there is going to offer you the protection and support you need. Microsoft Essentials is perhaps the closest to being protected for free. Still I install threats all the time with this client running so is it full proof? Not by a long shot. Spyware Doctor with antivirus is my favorite paid client if you decide on purchasing one
I don’t agree, AVG offers much more protection to incoming threats than Microsoft Essentials do, for example for this virus. Free products not always are bad products. Paying products sometimes are bad products too… I would recommend Norton, Mcafee, Pctools… and AVG or Avast if you want a free product without noticeable features.
About the virus itself, I ran in Safe Mode, exec CMD, c:, cd , dir /a … and then I saw a hidden directory called c:programdata … del c:programdataisecurity.exe … and thats all. Easier if you restore your system but remember to delete the file! The restore probably only avoid to run the virus at the start.
Last I tested AVG it offered almost zero up front protection. The paid version is good but the free version provides nothing more then a false sense of security.
You’re a life saver my man. Thank you!
Worked like a charm.thank you very much for that advice.
Looks like it worked for me – thank you.
Thank you sooo much!! Sooo simple and so effective!
Now installing Kaspersky… shame that I was too stingy to renew my licence for a few pounds to avoid that! Now nothing will do us apart! Meant Kaspersky and me of course 😉
Kaspersky is a good AV client. One of our top picks in the AV section.
Unknow someone with the ability to do so should sue the hell out of symantec and norton for all of this crap. I would but due to there crap I lost every dime I had
Why sue them? they are not the makers of these programs. Symantec is one of the most respected antivirus clients on the market. If anything people should thank them for all the research they have done and continue to do to combat viruses. They have helped to lead the industry in protection for many years.
What I want to know is, why doesn’t the FBI find and prosecute these assholes that put this software on your computer? Isn’t this the same thing as stealing? I have to pay money to buy their virus protection software that really does nothing other than just remove their software.
This shit is illegal, people have been prosecuted for it before.. I think it’s just not important enough for the FBI to get involved or something like that.
People are prosecuted for this kind of crime. You have to keep in mind that the makers of this malware are from several countries out side the US. It’s not like the FBI has any juristinction. Early this year with the help of several govremants and agencies a few huge malware creators were busted. It’s hard work to fight this kind of criminal activity. I know it seems like little is done but a whole lot of people are working on stopping these kinds of threats.
The end take home here is you need to protect yourself and not rely on others for protection. Purchase a decent Antivrus client and you will not have to deal with malware. Sounds a little mean but it’s the truth.
Isn’t Microsoft essentials decent enough?
In my opinion no because you get no support for the product or real time quick help when infected with a virus that Microsoft Essentials can not remove. With that said I personally think Micorsoft Essentials is the BEST free client on the market. I have thrown many viruses at it and it does a great job at blocking and removing. Also has good upfront protection. However zero day virus threats and drive by downloads tend to get through too often for my liking.
Microsoft owns N orton so they have no incentive to make a good product. If something happens they’ll just sell you Norton 2, and then 2.3, 3.5, 6.7, and so on and so on. It just like trying to get government to fix pot holes. 3 Billion dollars later the holes are still their and they are asking foir 10 times the money they did the last 30 times.
Microsoft does not own Symantec (Norton). Yes ALL paid clients renew annually unless you purchase an extended licences. This is the same with almost all manufacturers. It takes many people and many hours of work to create a solid antivirus client. It’s not something any single person could do on their own.
Software evolves over time. Think 98,2K,ME,XP,Vista,Win 7, Win 8. Same with MAC. As products change so do the holes. Most threats such as malware get in not from Microsoft it’s self but from other software installed on the Windows computer.
I hear what you are saying but with the software world getting so big and the internet becoming integrated into our everyday lives it’s only going to be harder and harder to create proper protection. If you want to blame someone on the price I would say the US should stop printing money and devaluating the currency. Then the price would be more stable.
According to the post above, several of us got infected through Orbitz, how can that be????
During the 90’s a member of the New York anti law and order family had lunch at the White House. Money changed hand 85 federal prosecuters were fired and list of new prosecuter appointed. Those guys are still in postion, and their record against disorganized crime isn’t that hot.
Law enforcement in Amerika is too busy checking into your sex, drug and R&R life. They have no time to go after crimes that have victims.
thanks Davemason50 worked for me to
thanks for your help
Just bought a NEW computer from Dell. It has this “Security Shield” on it?!?! What the F?>*!!! I Thought that Dell would want “repeat” business, Guess I was wrong. How does this happen to a new computer?
New systems do not have Security Shield installed on it. The program was installed only after you conected to the internet.
Found one on mine. The guide really helped. By the way, if the program starts on your computer, be sure to open up Task Manager to look for unfamiliar executables (.exe) running on your computer. Mine was urjpbxct.exe. Next you want end that process. The priority is low so if you are on an administrator account it will end. Next, follow the steps in the guide to delete the executable and get some antivirus software next time.
Do you have to buy this???
buy what?
Does this really work?
5 thumbs up, 170 tweets, 29 facebook likes, high rated article, several comments saying it works and thanks. That all should answer your question
When I got the security shield virus I restarted my computer, opened the REAL MS Security Essentials (click “Start”…it’s under “All Programs”) and ran a Full scan. I tried this several times, but I never finished the scan because the pop-ups faked me out into thinking that they had halted the real MSE scan. So, I kept clicking out of the pop-ups by hitting “control-alt-delete” and trying something else. Once I realized the MSE scan was still running under the virus pop-ups, I just ignored the virus alerts and pop-ups and let MSE do its thing. The pop-ups don’t do anything unless you click on them and will go away after about 60 seconds. They are all obvious because of the awful english, “Security Shield has found viruses at you system. We highly recommended to get license for Security Shield…”
The full Microsoft Security Essentials scan took over an hour and a half, but it found the virus, killed it and it didn’t cost me a dime. You just have to make sure you open and start a full MSE scan fast so the pop-ups don’t block your screen view (even if they do, just wait and they go away – although another will come a minute later).
I love the broken English these guys always use. They spend mega bucks infecting computers so you would think they would try a little harder to make their software look more legit.
Great the MSE worked for you. In most cases users will have AV software disabled by the malware. With that said, sounds like MSE was already on your computer when you got infected. If that was the case then it failed to block this threat. I would be interested in hearing back from you if it was already installed and up to date.
Thank you very much, man, my gf had this.
You are very welcome. Glad we could help get you sorted.
watch out for the name softaika
How do I find the restore program after starting in safe mode?
Same way as normal mode. Nothing different
can you help please? i can not get into safe mode…. after selecting Safe Mode, system loads drivers, but gets stuck at “mup.syst”, can not get Safe Mode.
I need to fix that first…please advise
Found them and deleted them in safe mode. EXCELLENT GUIDE. Today is my 5th day on the job and the VP had been working on it for a week. Thanks for making me look good! Great fix!
Making you look good is what we like to do
Thank you! Safe mode first, then system restore to earlier date – my computer is fine now =)
Love hearing feedback. Thanks for taking the time to comment
This seems to have worked for me. Thank you! I ran Malwarebytes after renaming the .exe and it found additional “rogue” traces that it removed. (I don’t have Stopzilla, is there something unique about that AV with regard to this virus?)
Honestly I have stopped recommending the product. Was working great at rmeoving threats for a while but they don’t seem to be keeping on top of things as of late. Spyware Doctor with Antivirus is the better choice. The new 2012 version kicks ass
Found the exe and removed it – thanks !!
Hi, got infected 6 Feb with McAfee installed. Full scan for viruses and malware did not pick it up & remove file. Used iPhone & found your site. We followed your advice found file, renamed it and deleted it. Worked like a charm. Thank you so much. You are a star!! Our file was located c:usersusernameAppDatalocal file name qsupa.exe.
I can’t find where documents and settings are. I did the safemode thingand it worked. But now what do I do?
Got to help me out here. What is your Operating system. Also please read the guide the paths are listed in there.
Thank you Davemason50. Your solution worked like a charm and best of all was absolutely FREE! YAHOO!!!!!
I was infected with Security Shield on my Laptop(unprotected) today. I decided to do a system restore and it seemed to disappear. I then installed Kaspersky Internet Security on the laptop (I had a spare product key lying around) and did every scan possible(Including trouble shooting for irregular settings caused by malware), nothing was detected. Is this enough to ensure that it has gone or are there other programmes/steps I should be using to ensure it’s all safe. Thanks! (Also, has this malware been known to attack your online banking etc? i’m very paranoid right now! >.<)
This threat does NOT steal any personal information like banking info or social info. It is always possible you were infected with something else beside this virus however Kasperky would of picked up those bigger threats. You are good to go. IF you want to run an extra scan using SPyware Doctor with Antivirus or Malwarebytes just to make sure you can. Just remove the client when you are done as Kaspersky on many other clients don’t play well together.
can you help please?
i can not get into safe mode…. after selecting Safe Mode, system loads drivers, but gets stuck at “mup.sys” and stops, can not get Safe Mode (win XP home)
i need to fix that first…please advise
You are going to need to use the Windows restore CD. Boot with that and run a checkdisc. If that does not resolve the issue you may attempt to restore Windows using the same Disc. Basically it’s like re-copying over the core Windows files. If you have data that is important to you I would advise you call a computer repair tech in to fix the system. You can also Google “mup.sys error” but I’m guessing you will see my two recommendations as the best repair options.
chckdisc didn’t help, i’ve done that. windows reinstall would fix it for sure but would also delete some stuff…
r u familiar with hirens cd? trying that but can not get updates for MB or SAS even though there is option for that…
I’m familiar with hirens cd. Did you do a search for mup.sys yet? I found this page that offers several ideas for you to trouble shoot down. http://www.aitechsolutions.net/mupdotsysXPhang.html . I would remove all USB devices and even remove most memory from the PC so you can eliminate those kinds of issues right away.
im using hirens (15.1) to get rid of security shield since i cant do it from safe mode… the only ativirus that seems to work from hirens is spy bot and SAS, but cant update definitions…both found some fake av but after rebooted from hard drive sec. shield rfeturned, so not all was removed…how to get net connection with hirens, and is it possible to IE instead of Opera?
thanks for the link, will check it out…
The fake AV is the least of your worries with the error message you are having. If you want to run an AV scan on it the best thing to do is just remove the drive and hook it up to a working PC and run an AV scan that way. You could also run a scan disk on the drive to see if that will repair the mup.sys issue but often times it can make things worse.
THANK YOU SOOOOOOOOOO MUCH!!!! 🙂 🙂 🙂
Glad we were able to help you out. Take a second to hit the FaceBook like button for us. Helps build trust. IF you do not have a facebook account you can help us by rating us high on http://www.mywot.com/en/scorecard/removevirus.org
Thank you sooo much! Mine was in systems32 too!
I’m just not computer savy so I couldn’t figure out how to follow the steps above (I couldn’t locate the .exe file. So I found this “If Security Shield appears on your screen, try “registration code” 64C665BE-4DE7-423B-A6B6-BC0172B25DF2 to disable the pop-ups and then delete Security Shield as soon as possible.” The registration code deactived the pop ups and I was able to get someone I know to connect remotely to my PC, they were then able to follow the steps above, and remove the virus from my PC. Thank you!!!
Hi, i’m running windows xp and i have that Security Shield virus. My system restore is not working, so i restarted in safe mode to delete the executable file. But i can’t find it. As a matter of fact, i can’t even find the “application data” branch in path that you noted above. Can you help me locate that executable file?
I’m running windows xp and have been infected with that virus. It has shut down my system restore so i restarted in safe mode. However, i’m having a hard time finding the executable file. As a matter of fact, i can’t even find the “application data” branch of the path you noted above. Can you help me locate the executable file?
Your operating system determines the path and were you need to look. What is your operating system? Also the Application Data folder for XP and App Data folder for Vista/Win 7 is a hidden folder. You must first un-hide hidden files and folders. We have a guide for this under the how to Guides section of the RV website. Let me know if you still need help after this.
i clean it with your help thank u!
after delete that file in c:/….user/Appdata and scan with Spyhunter is it enough or i should remove my windowns 7?
I would run one more full scan using Spyware Doctor with Antivirus to ensure you are virus free. If nothing major comes up I would say you are good to go.
im jans_sjj thanks for your replying i found your website awsome! i think i should explain more
yesterday i scan with Nod32 and i found that exact file which was in my appdata and in an unusual name i quarantinethat file then i removed it
today i installed your recommended anti virus Gozilla and in my appdata it doest found that file
is it enough for making sure? again thank you so much for ur helping i thought i should install another windows!
From what I read you are asking if you are still infected with the virus. If you want to be 100% sure I would run a virus scan with Spyware Doctor with Antivirus. Just got done testing it against Security Shield to ensure it is still working to pick up the latest traces and it did. If SDA says you are clean then you are good to go. NOD32 is a great client as well. If it’s the paid client I would also trust those results.
yes it is Nod32 smart security 5 with latest update with username and password 😉 is it enough?
i really like ur website!! is it any way to support?
You should be good to go. As for support, we review a wide range of software products under the review section of this site. If you ever need any software you can check it out. Purchasing a product through a link on our site will provide us with a commission in some cases.
im jans_sjj thanks for your replying i found your website awsome! i think i should explain more
yesterday i scan with Nod32 and i found that exact file which was in my appdata and in an unusual name i quarantinethat file then i removed it
today i installed your recommended anti virus Gozilla and in my appdata it doest found that file
is it enough for making sure? again thank you so much for ur helping i thought i should install another windows!
got mine from looking at porn
Porn is a sure way to get a virus. Never install any software or video codec if a adult website asks you to.
My friend got infected, and we can’t figure it out, spyware doctor doesn’t work
I just tested Spyware Doctor with Antivirus today and yes it does work. Got the latest variant and it caught every aspect of the threat. Ensure you have got the latest updates. Also do a FULL scan and not just the initial scan.
how did you test it? to do that you would have to infect yourself with a version of the virus. unless you can find somewhere you can get infected with the latest version of the virus you would have to use your own copy, and of course that one would get removed because your program has done it before. new iterations would be harder to remove.
Newer iterations are normally not harder to remove because the footprint is the same. Infecting a test computer is no big deal. It can also be run an a virtual environment so it won’t cause any harm.
Hi Guys I have just been hit with this b*****d software. The way I got rid of it was to reboot F8 into safe mode and run CCcleaner which is a free app
If I reboot my computer in safe mode and restore it a few days earlier, will that work, or be enough?
Will it work to remove the virus? Yes often times it will. Providing the virus did not disable this option. Many times it will.
Is it enough? You still will need to run a full virus scan to ensure your computer is virus free.
Hello, can someone help me please, i need to remove Security Sheild from my laptop, it appeared on my screen on the 29/2/2012, and ive tryed litrerly everythig, but its not going.. can some one please please help
thank you
Kind regards
Alfie
The picture is showing the version thats on my laptop
What is your operating system? What step in the guide are you having trouble on? Be as specific as you can about what you have done and what you are trying to do.
Ok so i believe I got this virus and thought I had it removed for the most part however i just went to turn on my laptop and got a disk check option which removed some index file and now when i try to start the computer it goes to start windows normally then loading then for a split second I get some blue screen and then im back at the repair windows and start windows normally options
sounds like your OS is corrupt. Boot into safe mode and run a system restore
You saved me, thank you! Found it, renamed it, no more pesky security shield warnings! Questions, first should I remove it from my recycle bin or is it disabled there? Also how do you know where you got it from, I also recently made a purchase from the orbitz site. How can I tell? And should I worry that I gave them my credit card info to purchase a flight??
I would clear out the recycling bin but for all intense and purposes the threat is gone. Ensure you run a full virus scan.
No way of telling exactly were you got infected from. Having a good antivirus client on the front end really protects you against these kinds of threats.
I would not be worried a whole lot about purchasing anything online while infected. I have tested this myself and have heard from many others that the program is not stealing personal information entered online. I would monitor the card closely over the coming weeks and ensure no unusual charges. If you want to be 100% confident you can always get a replacement card and cancel out the old one
I tried to do everything it said here but the Security Shield doesn’t let me save and run the Spyware Doctor, PLEASE HELP!!!
Thank you for the advice. That @##$%$ virus was driving me crazy.
Thank you everyone- wife picked up Security Shield at Orbitz (yay orbitz); spent long time researching, this thread was the most helpful. Got really nasty version- wouldn’t let me do anything- no applications, files all hidden, launching browsers was impossible. Launched in safemode with networking to download Malwarebytes; used that to clean off machine, quick scan and then full scan. Then swapped out new HOSTS file as well. Restarted; desktop still messed up, no programs in Start menu, but could search for programs and at least launch browsers; virus seemed to be gone, but wasn’t sure. Resorted to using Restore command from F8 safe boot, so lost a few days but seemed to work. Last step at the end was to reset all the folders to Folders-> View all. She has Windows 7, not used to it, so it took me a while to find that. After final restart (we are at 4 hours+ total time) our machine seems better. We were a little freaked when we couldn’t see all our pictures (most were backed up, but still….) but could see that the disk drive was pretty full, so it was just a question of restoring visibility.
Thanks a lot! It removed the virus, but I can still see the shortcuts on the desktop. They don’t have the icon. Should I delete them normally or should any precautions be taken?
delete normally. Shortcuts do not matter as the main .exe file is not valid any more.
Thanks a lot, jerdei. After removing the virus, the system remained very slow. So I took the advice of restoring the system and ran the antivirus again. It worked like a charm! Thanks again and to all other people that added their experiences, it sure helped.
I’m not seeing those executables in the file folders mentioned above on a Vista system…
The way i removed “security shield” is by restating computer and once entered my password i pushed “ctrl, alt, delete” choose task manager then i click on processes find “foyhnixes” (or something like that) right click, open file location. Before go into location it self make sure that “foyhnixes” is in blue color, click “end process” (which is in the bottom right corner of task manager window) Then look at the window, which should be opened when you clicked on file location earlier, and then delete the program! I hope it make some sense.
before the scan completes you can still use task manager in aplcations right click on scurity shield click on go to prosess it will highlight the prosess and slect end task then download malware bytes to clean the computer
I have just located the “security shield virus” running as a process on my computer under ysthinrp.exe*32 the file was located in my appdata/local folder. I thought i would post this because i noticed i could not find any info about this program running under this name before(ysthinrp.exe*32)
Wow…totally not cool. Do not use PC Tools Spyware dr that says it is free.
This is not a free removal of spyware.
I go through the download and it identifies the viruses but if you actually want to remove it, it costs money!!
Don’t waste time like I just did…
If you read the guide it clearly states that SDA needs to be registered in order for it to remove any threats. We also state this on EVERY page.
Make no mistake. The free manual method in the guide works like a charm as the 100+ comments suggest.
RemoveVirus.org does not recommend out free AV clients because NO free client on the market is sufficient enough to provide proper online protection.
The guide mentions SDA as our preferred AV client. You can also use it as the guide suggest to run a full scan to ensure you are no longer infected with anything else. This is a sure way to know if you have left over traced. From there you can manually remove them.
I apologize. I did not read the article thoroughly enough.
Is system restore supposed to usually take longer than an hour?
no. In most cases it may take 5-10 minutes. I would recommend booting into safe mode and selecting a different restore point. Doing the System Restore in Safe mode is your best option.