Coupcoup is another adware application that is put out by JustPlugIt, and it is sure to annoy you as much as the other pieces of computer junk that is created with that software. If you find evidence of this on your PC, you will want to remove it as soon as possible despite the fact that it promises some useful features for you.
Like many other adware programs, it will show unsolicited advertisements once it is installed. This program could even considered more malicious than adware because the clients completely control the applications and advertisements that are shown. Therefore, it is wise to remove it as soon as possible once you know
JustPlugIt has a reputation for distributing a wide range of nefarious software. Furthermore, the application supports creating programs on all the popular browsers like Internet Explorer, Google Chrome and Mozilla Firefox. Furthermore, the developers can customize their ads any time so there is no telling what kind of ads you will be redirected to if you are infected with Coupcoup.
Coupcoup is distributed by the InstallRex installers that you see associated with other malware and adware. It has also been found to be bundled with other programs like Amonetize. It has also been found to be bundled with browser hijackers put out by Websearch. If you do download and install programs from these sources, there is a good chance you will end up with Coupcoup or something similar on your system.
This program has been shown to collect private information as well. The information is mainly used to research your browsing habits and help the developers know what kind of ads to show you. But, it can be used to collect other information like usernames and email addresses. These advertisers will use all this data to learn what kind of ads to show you when you are browsing on the Internet.
Coupcoup wold be considered a malicious software and should be removed as soon as possible. If you leave it on your system, there is a good chance you will leave yourself open to further infections from other sources. This will make it more difficult to get rid of it and the other infections on your system.
Removing the program from your system can be done manually. The instructions are included below. However, if you would like an automated way to remove the software then we recommend SpyHunter to remove the software. You can download the software by clicking on the button below. You can download the software for free and scan your system for issues.
Uninstall Rotary Turners from Windows.
- Open up control panel by clicking on the start button in the lower left corner of your computer, and then going to Control Panel
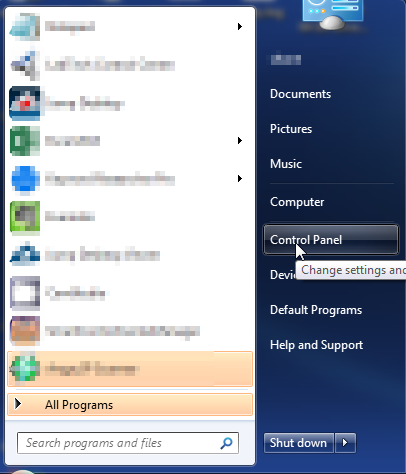
- Once, you are in Control Panel, go to the link labeled “Uninstall a Program”. If your computer does not look like the view below, you may have to sort by categories at the top right.
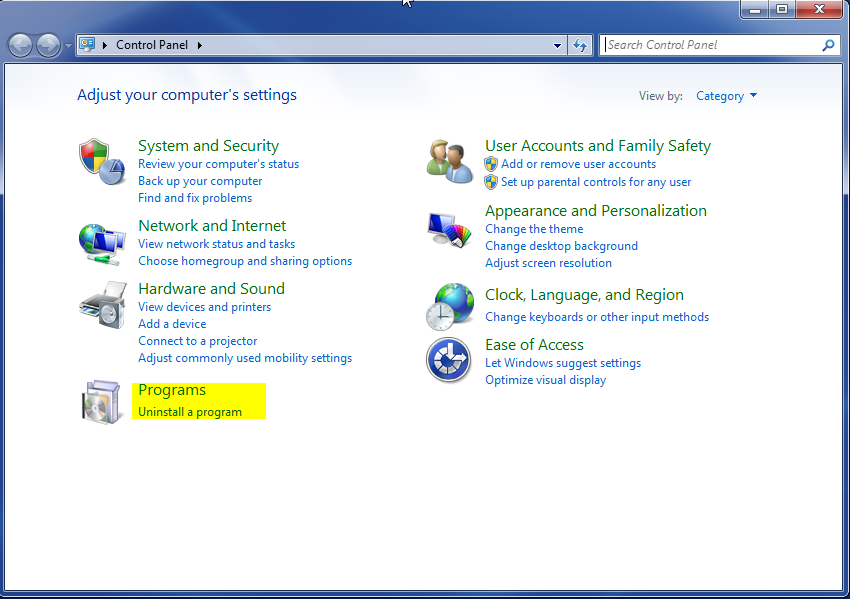
- Once in the uninstall programs section, look for the offending program. You can scroll by date installed to find programs that were installed recently. This may be a clue as to what the offending program is. Once you have found the program, highlight it and select “Uninstall” to remove
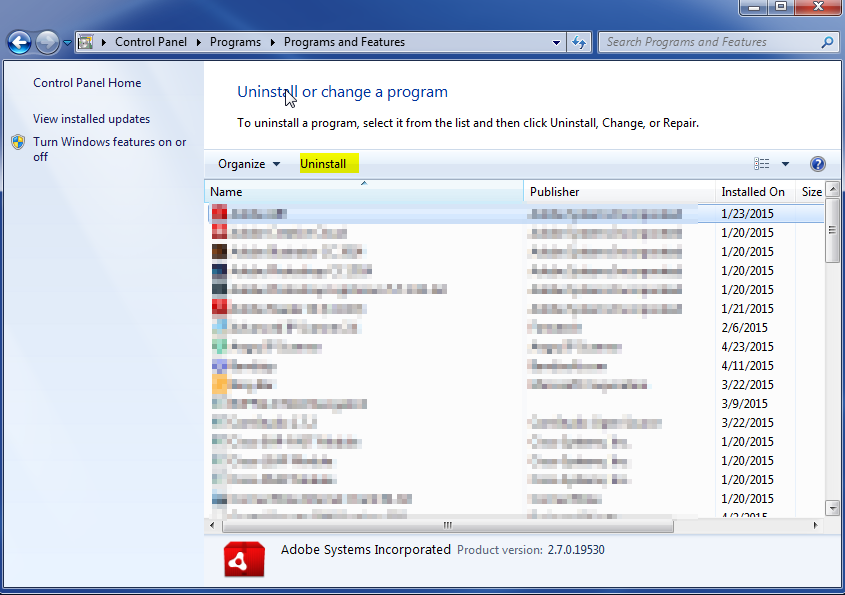
Once you have done this, you will need to go into your browser and set it to its default settings to remove the other changes it made. You will also want to scan your computer to make sure no new issues were introduced by the vulnerability. A good tool to use for this is MalwareBytes. If you already have a virus scanner, you should run this as well.
