Select operation of the CD-ReWriter as an IDE master or slave, or for cable select, via the configuration jumper at the rear of the unit.
In this case the drive’s factory setting is as a Master.
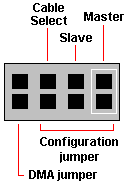
To configure the drive as a Slave, move the jumper to the middle set of pins, leaving the other pins uncovered. To change the drive for Cable Select, move the jumper to the left set of pins.
This particular drive has shipped from the factory with no DMA jumper installed. The empty pins mean the drive is set to Ultra DMA, a setting that will work in most cases. However, the default Ultra DMA setting may be inappropriate for some older motherboards, causing the computer to hang or crash. If this happens, the setting may be changed to Multiword DMA mode by jumpering the two pins just to the left of the configuration jumper.
The Cable Select jumper position sets the drive to use the CSEL signal from the IDE interface for configuration. This signal automatically selects the correct Master/Slave setting. However, use of CSEL require that you have:
- a computer that supports CSEL
- a special CSEL cable for IDE connector.
With Cable Select, the Master and Slave designations are determined not by jumpers, but by the actual connectors on the CSEL cable. The connectors are identified as Master or Slave.
Note that if any device is jumpered as Cable Select, then both devices on that cable must be jumpered in the same way.
- Drive Installation Terminology
- CD-RW Installation Intro
- CD-RW Installation Configuration
- CD-RW Installation Mounting
- CD-RW Installation Connection
- CD-RW Installation Bios Setup
- CD-RW Burning Software
- CD-RW Installation Optimization
- Floppy Installation Intro
- Floppy Installation Mounting
- Floppy Installation Connection
- Floppy Drive Installation BIOS Setup