RecipeSeach Toolbar is a plugin for your browser that comes from the Mindspark family of toolbars. This plugin may be a risk to your computer, so it is recommended that you remove this toolbar from your system. The catch to the toolbar is that offers you free recipes and cooking tips. But, as usual, nothing is without risk in the world of freebies. This software may come bundled with other software that will cause malware infections and other issues for your computer.
If you have installed the RecipeSearch Toolbar your default home page will be changed to Ask.com without you doing so. Home pages changing like that are an obvious tip off that some sort of malware or spyware has been installed on your machine. Therefore, it is a good idea to remove it as soon as possible.
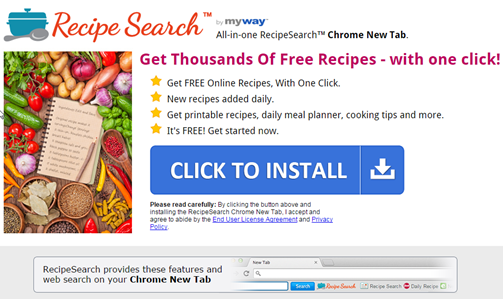
The toolbar can be downloaded directly from downloadrecipesearch.com. But, if you didn’t know about it it more than likely was installed as a bundle with something else. This is why you should always choose to do the custom installation when installing items. Then you can pick and choose what gets installed.
RecipeSearch Toolbar is a form of spyware. It will allow people to monitor your online browsing and searching habits. Many times this is simply used for marketing information. But the behavior of this toolbar makes your PC vulnerable to other information theft.
Removing RecipeSearch Toolbar is not too difficult. We have included the process below. However, if you want a simple way to remove the malware from your system you should check out SpyWare Hunter. It is a free tool that will identify any malware or spyware like RecipeSearch Toolbar that is found on your system. Just click on the orange banner below.
Uninstall RecipeSearch Toolbar from Windows.
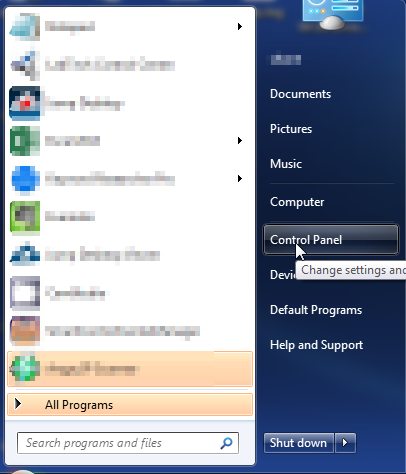
- Open up control panel by clicking on the start button in the lower left corner of your computer, and then going to Control Panel
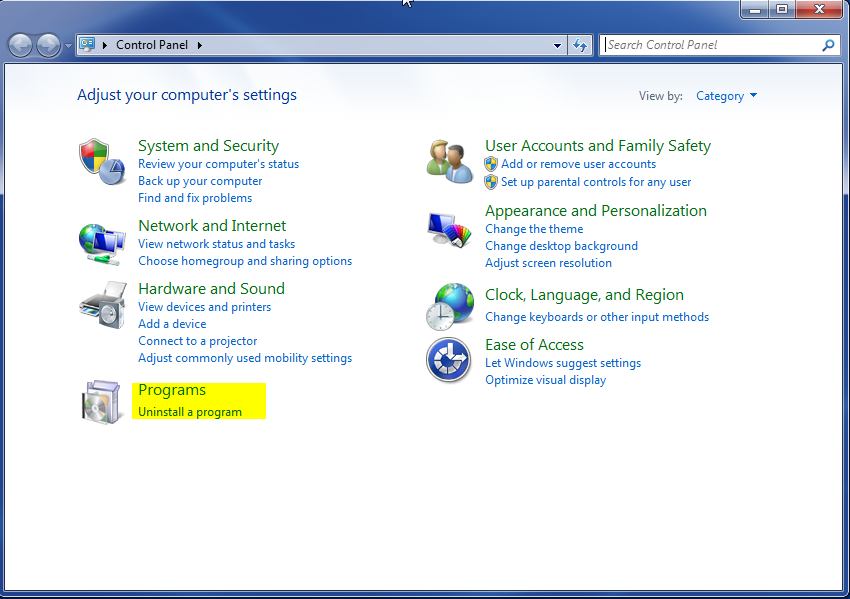
- Once, you are in Control Panel, go to the link labeled “Uninstall a Program”. If your computer does not look like the view below, you may have to sort by categories at the top right.
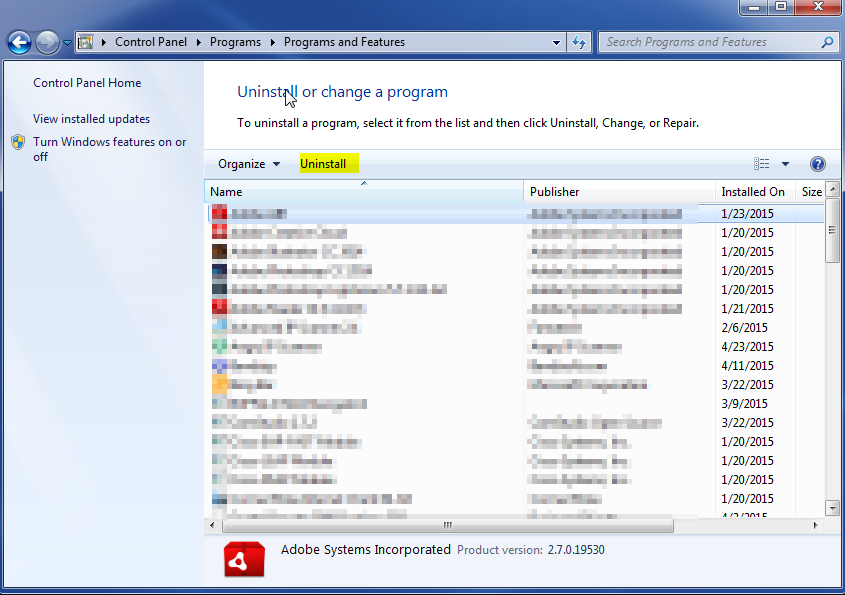
- Once in the uninstall programs section, look for the offending program. You can scroll by date installed to find programs that were installed recently. This may be a clue as to what the offending program is. Once you have found the program, highlight it and select “Uninstall” to remove
Once you have done this, you will need to go into your browser and set it to its default settings to remove the other changes it made. You will also want to scan your computer to make sure no new issues were introduced by the vulnerability. A good tool to use for this is MalwareBytes. If you already have a virus scanner, you should run this as well.
