 A program called Browser Security has to be a good idea, right? Its advertised to protect you online afterall. Well, the truth is that this is one program that you want to stay away from and remove as soon as possible. This program is distributed through some rather dubious methods, and it is nothing more than a potentially unwanted program.
A program called Browser Security has to be a good idea, right? Its advertised to protect you online afterall. Well, the truth is that this is one program that you want to stay away from and remove as soon as possible. This program is distributed through some rather dubious methods, and it is nothing more than a potentially unwanted program.
It is advertised as a tool that will alert you to any security issues and let you know if your computer is being threatened with issues. But, the truth is that it is a program that you will want to remove as soon as it comes to your attention. It is another piece of useless software that has no value whatsoever.
When Browser Security is installed in your system it begins making to your web browser and ads a browser extension. It works in Google Chrome, Mozilla Firefox and Microsoft Internet Explorer. In other words, all of the major browsers are impacted by the software and you are vulnerable no matter what your browser is. As we mentioned earlier, the extensions as advertised as a tool that will block security issues and alert you to potential issues. But, the fact is that it really does nothing. It has been shown to miss several issues. That is because the real purpose of the program is not to protect machines. That is just a lure to get you to install the software.
You can download the website directly from the website, but that is not its main form of distribution. Its main way of getting spread is through software bundles. Typically, it is bundled with other software that you are electing to download. But, other software, like Browser Security, is snuck in to the bundle.
It is a good idea to use custom install options whenever possible. This will give you the opportunity to skip extra software. But, even when using the custom installs, you need to be careful because they will try to trick you into installing extra software
The removal process of Browser Security is not too difficult, but care should be taken. If you do not do it correctly, you will be under the false assumption that the software was removed when it still continues to run. If you would like an easier way to remove the software, we recommend using SpyHunter to remove it. This is a piece of software that will scan your computer for free and report any problems. You can find the program by clicking on the link below.
Uninstall Browser Security from Windows.
- Open up control panel by clicking on the start button in the lower left corner of your computer, and then going to Control Panel
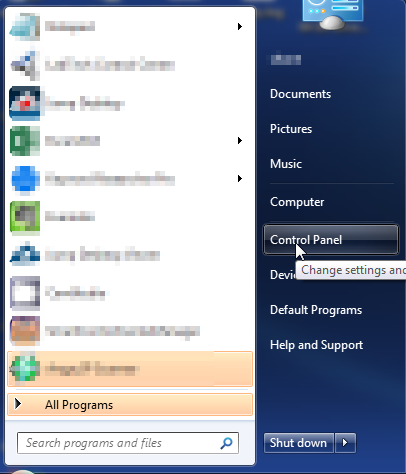
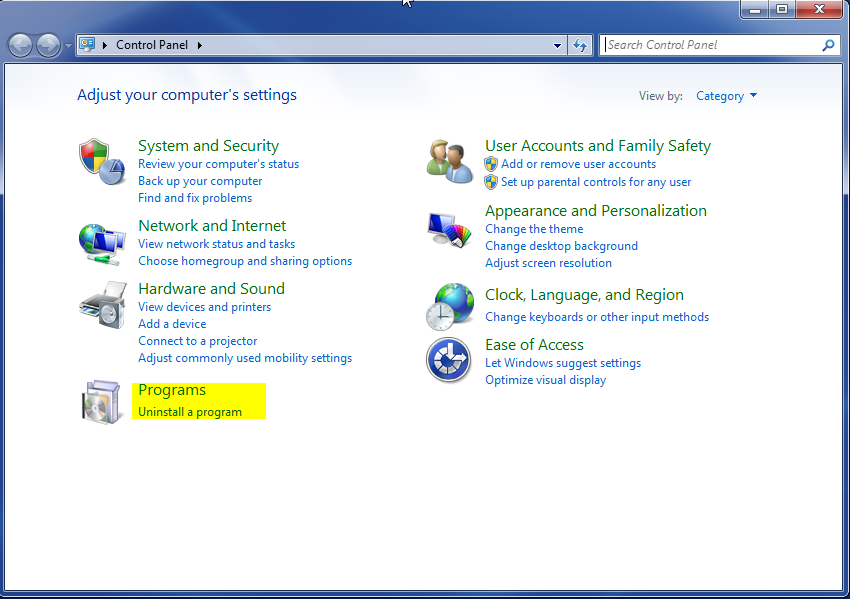
- Once, you are in Control Panel, go to the link labeled “Uninstall a Program”. If your computer does not look like the view below, you may have to sort by categories at the top right.
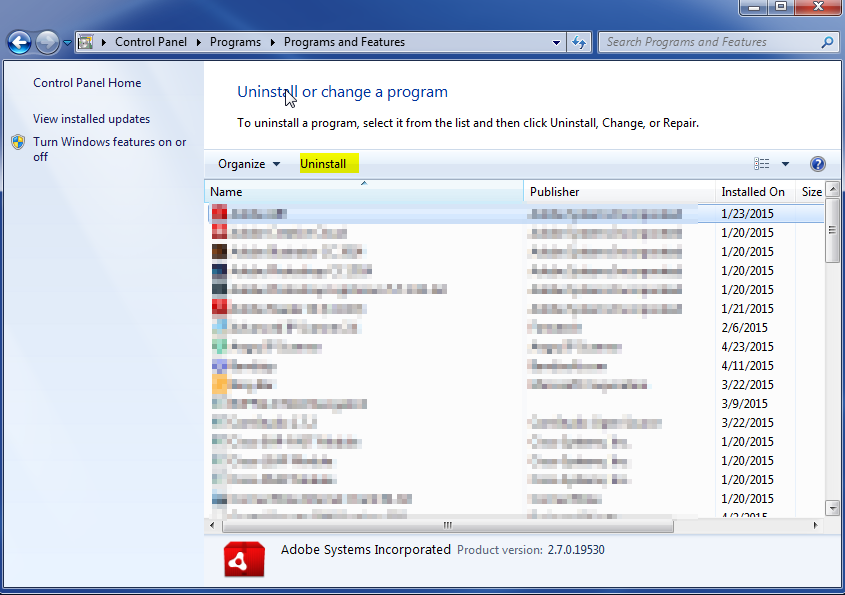
- Once in the uninstall programs section, look for the offending program. You can scroll by date installed to find programs that were installed recently. This may be a clue as to what the offending program is. Once you have found the program, highlight it and select “Uninstall” to remove
Once you have done this, you will need to go into your browser and set it to its default settings to remove the other changes it made. You will also want to scan your computer to make sure no new issues were introduced by the vulnerability. A good tool to use for this is MalwareBytes. If you already have a virus scanner, you should run this as well.
