Streaming is the technique used to transfer data in linear and helical scan tape drives, which operate by reading an entire track thousands of bytes long in a single pass of a Read head at a fixed tape speed. In order for such drives to operate at peak efficiency, the host must be able to keep the drive’s buffer full. A slow host or a busy SCSI bus can cause the tape drive to cease streaming, forcing the drive to reverse, or backhitch, before resuming the write operation. This not only impairs overall tape-drive performance, but also places additional stress on the media.
Ecrix Corp’s VXA technology solves this problem by using variable speed operation, essentially matching the speed of the tape to that of the host, thereby optimising tape drive performance and minimising undue stress on the media. Announced in late 1999, VXA is the first new tape technology in years to take an entirely different approach to data recording. Instead of the long blocks of streaming data used by most tape formats, VXA breaks long strings of data into small data units, then adds a wrapper of verification data, building small data packets – in what the company refers to as Discrete Packet Format (DPF) – before recording it on the media.
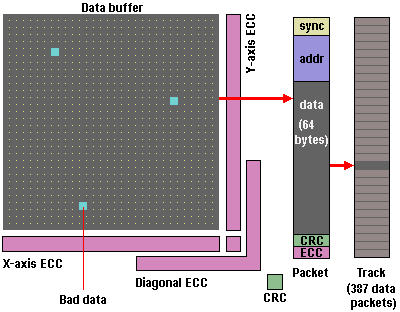
DPF allows the packets that comprise a data string to arrive at different times in the data buffer and still be efficiently reassembled into their original string order. Each data packet includes 64 bytes of user data, a synchronisation marker, unique address information, Cyclical Redundancy Check (CRC) code and Error Correction Code (ECC). Each track consists of 387 individual data packets recorded and read through a special buffer array. Two overlapping sets of tracks are written by the two pairs of heads on the drum. The first head in each pair writes the data. The second head performs a Read-After-Write to check the data integrity.
VXA employs four-level error correction which is applied in two phases. First, each packet includes a Reed-Solomon ECC which can correct small errors typically caused by noise or phase shifts. Second, when the packets are collected in the buffer segment, they form an array which employs a three-dimensional Reed-Solomon ECC (X-axis ECC, Y-axis ECC and Diagonal ECC).
The combination of DPF, variable tape speed operation and an overscanning technique which allows data to be read from any physical location on the tape, without having to follow tracks from beginning to end, result in a technology which is fast, reliable and highly immune to media errors. Initial drives operated at 6MBps, provided a maximum compressed storage capacity of 66MB and were shown to be capable of reading tapes that had been frozen and immersed in boiling water.