Phoneline networking takes advantage of unused transmission capacity to transmit data over existing telephone wires. They transmit information at frequencies well above that of plain old telephone service (POTS) or digital services like ISDN and DSL, so the network does not interfere with the normal use of the phone line for voice, fax or Internet services running over the same telephone circuit. Nor do these other phoneline services affect network data transmission quality.
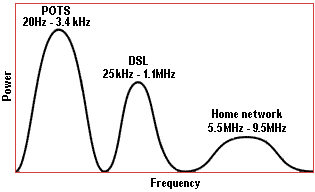
The technology used to divide up shared bandwidth is frequency division multiplexing (FDM). This well-established technique divides up the total bandwidth into different frequency bands, called channels, using frequency-selective filters. Each of the different types of traffic – power, analogue voice and digital information (including data, audio and video) – use different channels.
The initial Home Phoneline Networking Alliance (HomePNA) specification – released in the autumn of 1998 – adopted the IEEE 802.3 media access method, essentially delivering 1 Mbit/s Ethernet over phone lines. The subsequent HomePNA 2.0 specification – finalised in late 1999 – takes advantage of digital signal processing (DSP) technology embedded in silicon to offer consistently higher performance, better adapt to poor line conditions by continuously boosting signal strength and improve filtering of noise (interference) from nearby appliances. HomePNA 2.0- based products can support transfer speeds of up to 10 Mbit/s, ten times faster than HomePNA 1.0- based products.
In a typical home phoneline network internal or external network adapters are installed in each PC, which are plugged into a nearby phone jack. Printers or other peripherals – including simultaneous access to the Internet via a single 56 Kbit/s analogue, ISDN, cable or DSL modem – can then be shared through a connected PC.
Phoneline networking works best in homes where the computers are located in different rooms near phone jacks on the same circuit – that is, using the same telephone number. The fact that each home has a unique phone circuit from the telephone company’s central office ensures a high level of network security.