The Institute of Electrical and Electronics Engineers (IEEE) ratified the original 802.11 specification in 1997 as the standard for WLANs. That version of 802.11 provided for 1 Mbit/s and 2 Mbit/s data rates and a set of fundamental signalling methods and other services. The data rates supported by the original 802.11 standard were too slow to support most general business requirements with and did little to encourage the adoption of WLANs. Recognising the critical need to support higher data-transmission rates, the autumn of 1999 saw the IEEE ratify the 802.11b standard (also known as 802.11 High Rate) for transmissions of up to 11 Mbit/s.
802.11 defines two pieces of equipment, a wireless station, which is usually a PC equipped with a wireless network interface card (NIC), and an access point (AP), which acts as a bridge between the wireless and wired networks. An access point usually consists of a radio, a wired network interface (such as IEEE 802.3), and bridging software conforming to the 802.1d bridging standard. The access point acts as the base station for the wireless network, aggregating access for multiple wireless stations onto the wired network. Wireless end stations can be 802.11 PC Card, PCI, or ISA NICs, or embedded solutions in non-PC clients (such as an 802.11-based telephone handset).
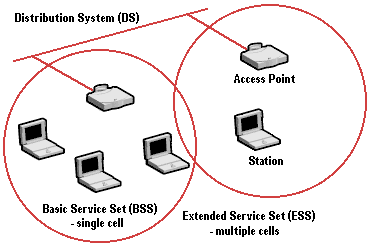
The 802.11 standard defines two modes: infrastructure mode and ad hoc mode. In infrastructure mode, the wireless network consists of at least one access point connected to the wired network infrastructure and a set of wireless end stations. This configuration is called a Basic Service Set (BSS). An Extended Service Set (ESS) is a set of two or more BSSs forming a single subnetwork. Since most corporate WLANs require access to the wired LAN for services (file servers, printers, Internet links) they will operate in infrastructure mode.
Ad hoc mode (also called peer-to-peer mode or an Independent Basic Service Set, or IBSS) is simply a set of 802.11 wireless stations that communicate directly with one another without using an access point or any connection to a wired network. This mode is useful for quickly and easily setting up a wireless network anywhere that a wireless infrastructure does not exist or is not required for services, such as a hotel room, convention centre, or airport, or where access to the wired network is barred (such as for consultants at a client site).
The three physical layers originally defined in 802.11 included two spread-spectrum radio techniques and a diffuse infrared specification. The radio-based standards operate within the 2.4 GHz ISM band. These frequency bands are recognised by international regulatory agencies, such as the FCC (USA), ETSI (Europe), and the MKK (Japan) for unlicensed radio operations. As such, 802.11-based products do not require user licensing or special training. Spread-spectrum techniques, in addition to satisfying regulatory requirements, increase reliability, boost throughput, and allow many unrelated products to share the spectrum without explicit co-operation and with minimal interference.
The original 802.11 wireless standard defines data rates of 1 Mbit/s and 2 Mbit/s via radio waves using two different – mutually incompatible – spread spectrum transmission methods for the physical layer:
- With Frequency Hopping Spread Spectrum (FHSS), a transmitting and receiving station are synchronised to hop from channel to channel in a predetermined pseudorandom sequence. The prearranged hop sequence is known only to the transmitting and receiving station. In the U.S. and Europe, IEEE 802.11 specifies 79 channels and 78 different hop sequences. If one channel is jammed or noisy, the data is simply retransmitted when the transceiver hops to a clear channel.
- Under Direct Sequence Spread Spectrum (DSSS), each bit to be transmitted is encoded with a redundant pattern called a chip, and the encoded bits are spread across the entire available frequency band. The chipping code used in a transmission is known only to the sending and receiving stations, making it difficult for an intruder to intercept and decipher wireless data encoded in this manner. The redundant pattern also makes it possible to recover data without retransmitting it if one or more bits are damaged or lost during transmission. DSSS is used in 802.11b networks.
At the OSI data link layer 802.11 uses a slightly modified version of the CSMA/CD protocol known as Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) or the Distributed Co-ordination Function (DCF). CSMA/CA attempts to avoid collisions by using explicit packet acknowledgement (ACK), which means an ACK packet is sent by the receiving station to confirm that the data packet arrived intact.
It works as follows. A station wishing to transmit senses the air, and, if no activity is detected, the station waits an additional, randomly selected period of time and then transmits if the medium is still free. If the packet is received intact, the receiving station issues an ACK frame that, once successfully received by the sender, completes the process. If the ACK frame is not detected by the sending station, either because the original data packet was not received intact or the ACK was not received intact, a collision is assumed to have occurred and the data packet is transmitted again after waiting another random amount of time.
CSMA/CA thus provides a way of sharing access over the air. This explicit ACK mechanism also handles interference and other radio-related problems very effectively. However, it does add some overhead to 802.11 that 802.3 does not have, so that an 802.11 LAN will always have slower performance than an equivalent Ethernet LAN.