Unveiled in the summer of 2004, SLI (Scaleable Link Interface) is Nvidia’s revolutionary approach to 3D graphics scalability which exploits the additional bandwidth and features of the PCI Express bus architecture to allow two graphics cards to operate in a single PC or workstation, thereby dramatically increasing graphics horsepower and delivering as much as 2x the performance of a single GPU configuration.
SLI joins two identical Nvidia graphics cards by way of a compatible motherboard sporting a pair of PCIe x16 slots, the company’s SLI-compatible PCIe graphics cards having a row of pins along their top edge that accept a daughter card that connects the cards, straddling the gap between adjacent card slots.
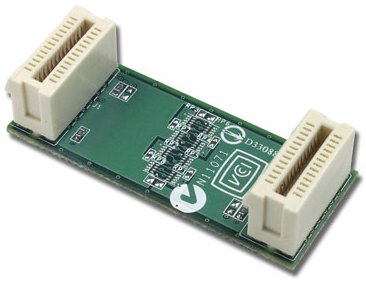
The SLI-compatible cards feature hardware and software innovations within their GPU and MCP (media and communications processor) components which facilitate use of the high-speed digital interface for the synchronisation and transfer of image information.
The way the rendering task is split between the two cards is not fixed, as it would be, for example, if either card were to be responsible for rendering either odd or even lines. Rather, each card renders whole sections of the screen at a time, the dynamic load balancing technique employed being designed to allow each card to work at as near to its full capacity as possible.
Nvidia was to enjoy a spell in which it was unchallenged in the dual graphics card arena. However, given its success, it was no surprise when arch-rival ATI launched its answer to SLI a few months down the line.
- How Do Computers Make Pictures?
- Graphic Card Resolution
- Graphic Card Colour Depth
- Graphic Card Components
- Graphic Card Memory
- Graphic Card Driver Software
- 3d Accelerated Graphic Cards
- Graphic Card Geometry
- 3D Rendering
- FSAA Graphic Card Technology
- Digital Graphic Cards
- DVI Graphic Cards
- HDCP Technology
- Graphic Card HDMI Ports
- Graphic Card Display Port
- Unified Display Special Interest Group
- DirectX
- OpenGL technology
- Direct3D
- Talisman
- Fahrenheit Graphic Cards
- SLI Technology
- CrossFire Graphic Cards