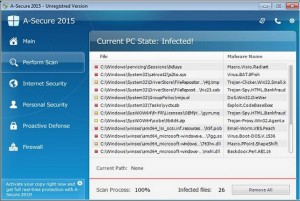
 A-Secure 2015 is actually a fake and deceiving anti-virus program that will make you believe it’s a legitimate anti-virus protection program starting off by asking you to download its trial version and analyzing your computer. To your surprise it will tell you that your system is heavily infected either by malwares, Trojans and other computer program related risks. The bad thing is, this rogue application will attack your computer’s operating system once you allow its program to run and will infect your email attachments, torrent downloads and security features just to gather information from your computer’s system.
A-Secure 2015 is actually a fake and deceiving anti-virus program that will make you believe it’s a legitimate anti-virus protection program starting off by asking you to download its trial version and analyzing your computer. To your surprise it will tell you that your system is heavily infected either by malwares, Trojans and other computer program related risks. The bad thing is, this rogue application will attack your computer’s operating system once you allow its program to run and will infect your email attachments, torrent downloads and security features just to gather information from your computer’s system.
The Things A-Secure 2015 Do
Once the A-Secure 2015 software has gathered enough data from your computer it will generate a long list of detected malware that supposedly exist among your files and your computer’s structure. You may believe that what it tells you are all true because it shows up some of your files that are really there. This program can imitate legitimate computer security scanners and expose to you a list of the unnecessary files that posed risks to your system but all of these are already pre-written into the A-Secure 2015’s organization.
You must also know that A-Secure 2015 has actually no virus definition database so this does not definitely have the capability to detect any form of intrusive program that may be lurking inside your computer. Once you activate it, it will show you in its ‘security scan list’ the pre-installed list of malwares, adwares, viruses, Trojans and you name it, the A-Secure 2015 has it in its list. Because you may get scared of what’s prowling in your system, you may be convinced to purchase a fake license key to download the full version and that’s the real purpose of the cyber criminals who created A-Secure 2015. They get your money and you pay your own risks.
And as expected, the supposedly full version operates full time and always active. However, you will notice that there will be no changes in the performance of your computer. Installed or not, the program will not be doing anything good but instead, you may even get exposed to hackers who may be the creators of the program themselves. Your personal credentials will also be at high risk once you have the program running. So instead of cleaning out your computer’s system completely, you have added another infection to your computer through the A-Secure 2015 fake antivirus program.
A-Secure 2015 is categorically among the Braviax/FakeRean bogus antivirus programs family. All that belong in this family are highly capable of running extensive infections to Windows 7, Windows 8 and Windows XP operating systems. The Braviax family are known for their capability in modifying their names based on the OS of the computer they are installed.
In its history, there are instances that Windows 7 users would see the fake antivirus program Sirius Win 7 Antivirus 2014 and on Windows 8 this becomes Sirius Win 8 Antivirus 2014. But with A-Secure 2015, its name don’t change with all the OS it deals with. The worst thing that it can do to your computer is infecting it with Trojans which can relatively shut down your system or there will be constant pop-ups of fake online security warnings.
Fight It
If you see an online message telling you that your computer has been detected to be infected with risky programs, don’t ever download anything especially the trial version of A-Secure 2015. Always update your antivirus security features and rely only to legitimate anti-virus and anti-spyware programs that were proven by millions of PC users to be authentic, honest and will really clean your system fast and efficient. So far the most reliable anti-spyware program we can recommend to deal with A-Secure 2015 fake antivirus program is the SpyHunter.
Spyhunter is an honest-to-goodness powerful anti-spyware application that runs on real-time. Certified by West Coast Labs’ Checkmark Certification System, it is configured for your computers’ optimal protection and fights against all malicious threats. Even you are an average computer user there is no complication in activating the program. Even the latest evolution of malwares and viruses, these can be detected and eliminated. It can also detect and delete rootkits which are folders that hide encrypted spyware and are really hard to detect.
Nonetheless, if you have already installed A-Secure 2015 in your system and finding it hard to remove it altogether, or being bugged with pop-ups that really bothers you, try SpyHunter. This is also effective against Trojan viruses that can crash your whole computer system.