Hot Finder is another browser hijacker that can make your browsing experience annoying and cause issues for your PC. Installing this hijacker will change your browser homepage to hot-finder.com and will change your default search engine to Yahoo.
Like many other hijackers, the software is not malicious in nature. But, it will add the hot-finder url to the end of everyone of your shortcuts. This can be annoying and can be confused with virus-like behavior. Not only will it change the shortcuts on your desktop, it will also change them in your Windows Start menu.
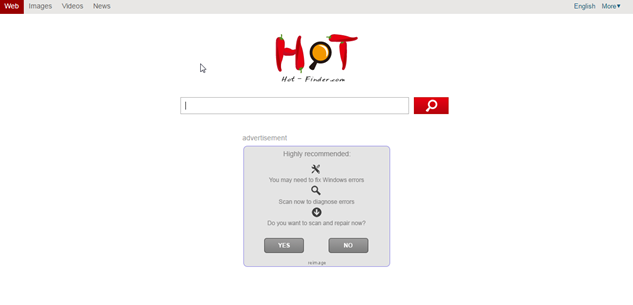
This hijacker is similar to many others in that it will use their homepage which is full of ads. It will show banner ads and sponsored links in your search results. These ads help make money for the people who create the hijacker. They get paid from people clicking on the ads that are shown as banners, popups, and inpage links.
Again, this is not a virus, but it does have some traits of a virus. The main one is that it can reach into the operating system and make changes. This can open doors for other issues later on.
The changes can be made to all popular browsers on the machine. This includes Google Chrome, Internet Explorer and FireFox. It will also attempt to lock down the browsers to prevent changes from the user and other competing software.
The most likely source of infection was from the installation of another piece of software. It was most likely bundled with free software that you found on a download site like Download.com or Snapfiles. Removing these programs will not remove the Hot-Finder virus from your machine.
The best thing to do when installing software from these free sites is to use the custom installation. This will give you the ability to deny installation of extra programs like the Hot-Finder.com BHO. If you choose the default install it will assume you want it installed and proceed to do so.
If you need an easy way to remove the malware from your system, we recommend SpyHunter. It is an easy, automated way to remove these types of issues from your computer.
iStartSurf is typically installed in bundled software. Many times it is bundled in video recording software, download manager and PDF creators. Unfortunately, even if you find out what it was bundled with and uninstall it, it will not remove the iStartSurf malware. Therefore, it is best to follow the directions below to help remove the program from your system.
Uninstall iStartSurf from Windows.
- Open up control panel by clicking on the start button in the lower left corner of your computer, and then going to Control Panel
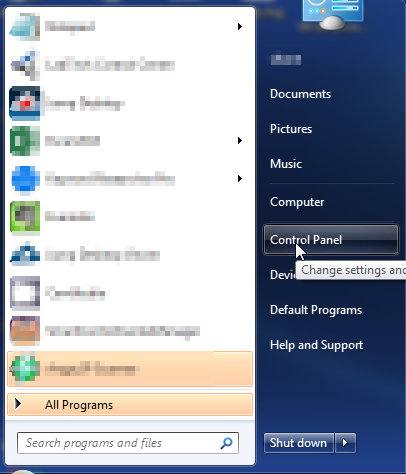
- Once, you are in Control Panel, go to the link labeled “Uninstall a Program”. If your computer does not look like the view below, you may have to sort by categories at the top right.
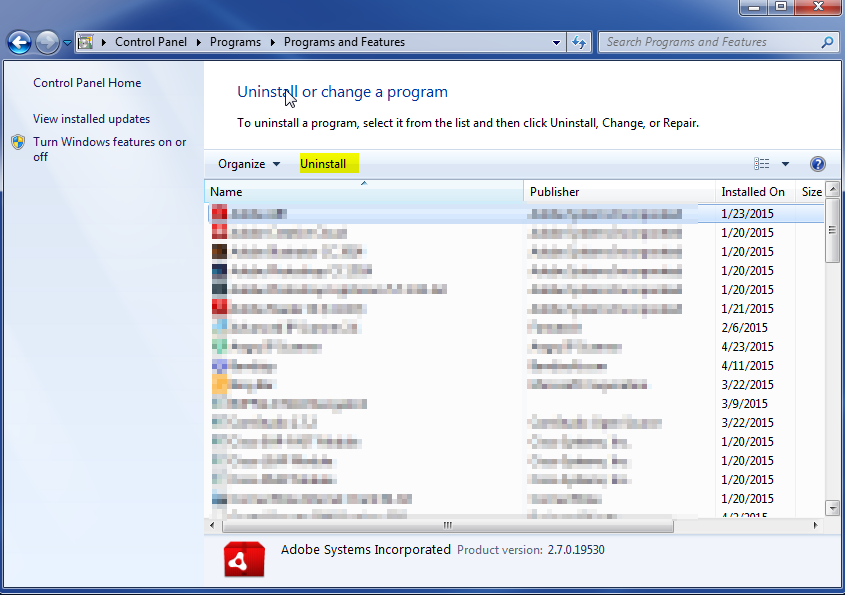
- Once in the uninstall programs section, look for the offending program. You can scroll by date installed to find programs that were installed recently. This may be a clue as to what the offending program is. Once you have found the program, highlight it and select “Uninstall” to remove
Once you have done this, you will need to go into your browser and set it to its default settings to remove the other changes it made. You will also want to scan your computer to make sure no new issues were introduced by the vulnerability. A good tool to use for this is MalwareBytes. If you already have a virus scanner, you should run this as well.
