You may be getting random popups in your browser from a company claiming to be MSTechSupport.info. These can happen inside any browser like Internet Explorer, Chrome or Firefox. This is a scam trying to trick you into thinking there is a company on the other end ready to help you.
It is caused by extensions within the browsers. It is installed when you install other free software. It is bundled with that software and installed without your knowledge if you do not pay close attention during the installation process.
When you are infected with this virus you will get a popup that states your computer is, in fact, infected with a virus. They will then give you a phone number that you can call to have your computer cleaned for $199. The funny part is your computer really is infected. But, they don’t the point is to make you think it is infected with something else.
You may also see advertising banners inserted into the pages that you view. If you visit the page often these may look strange to you because you had not seen the ads before. However, they may look natural if you have never been to the page before. The virus will also turn text into links. Furthermore, you will get popups advertising other products.
If you need an easy way to remove the malware from your system, we recommend SpyHunter. It is an easy, automated way to remove these types of issues from your computer.
It is a good idea to always pay close attention when installing free software. Try to always use the custom installer so you can see what other programs are being installed. And, read the directions closely. They will try to trick you with what button to click on.
How To Remove MSTechSupport.Info
- Open up control panel by clicking on the start button in the lower left corner of your computer, and then going to Control Panel
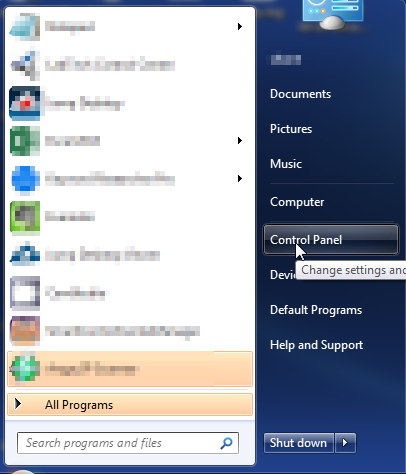
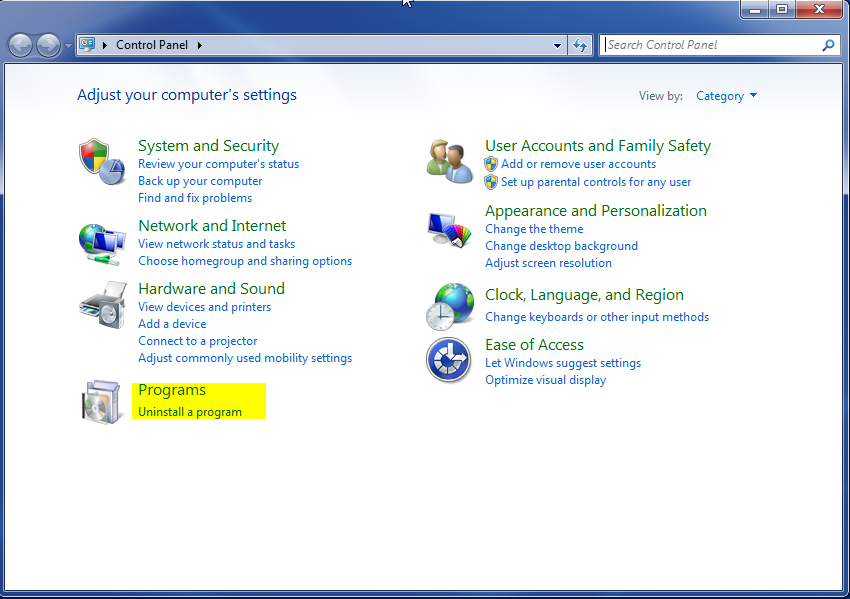
- Once, you are in Control Panel, go to the link labeled “Uninstall a Program”. If your computer does not look like the view below, you may have to sort by categories at the top right.
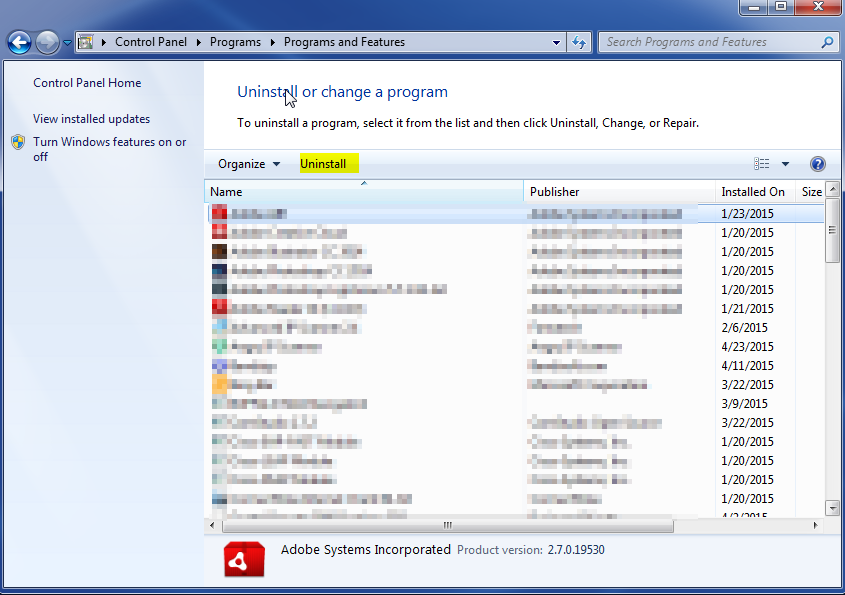
- Once in the uninstall programs section, look for the offending program. You can scroll by date installed to find programs that were installed recently. This may be a clue as to what the offending program is. Once you have found the program, highlight it and select “Uninstall” to remove
Once you have done this, you will need to go into your browser and set it to its default settings to remove the other changes it made. You will also want to scan your computer to make sure no new issues were introduced by the vulnerability. A good tool to use for this is MalwareBytes. If you already have a virus scanner, you should run this as well.
