iStartSurf is another bothersome browser hijacker that is promoted by free download. Like many other hijackers, it will change your browser homepage when it installs itself. It will change it to iStartSurf.com and it will change the default serch engine to Yahoo.
This may not seem like a big deal since many other programs do the same thing. However, it will append the httP//istartsurf.com to the end of all the shortcuts on your desktop and in the Windows Start Menu. It is very invasive and annoying.
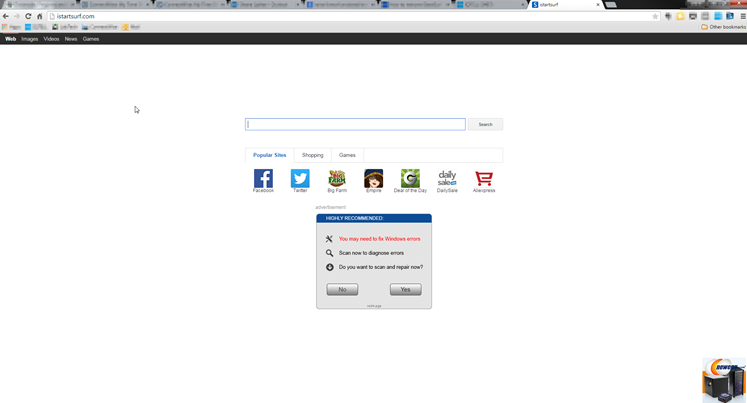
The iStartSurf.com homepage will display advertisements when you arrive. It will also show sponsored links in your search results. It serves these by monitoring your searches from the past. The purpose of the malware is to increase ad revenue and raise page rank for sites to help them with ranking in more legitimate search engines.
iStartSurf.com would not be classified as a traditional virus. But, it does have several traits of a virus. It has rootkit capabilities. And, it can interfere with the users because it slows down computers and can cause popups and other annoyances.
You will see banners, search links, pop-ups, pop-unders and intext advertising. This will be found on popular search engines like Internet Explorer, Firefox and Chrome. It can also lock down the browser to keep you from making changes in the browser.
If you need an easy way to remove the malware from your system, we recommend SpyHunter. It is an easy, automated way to remove these types of issues from your computer.
iStartSurf is typically installed in bundled software. Many times it is bundled in video recording software, download manager and PDF creators. Unfortunately, even if you find out what it was bundled with and uninstall it, it will not remove the iStartSurf malware. Therefore, it is best to follow the directions below to help remove the program from your system.
Uninstall iStartSurf from Windows.
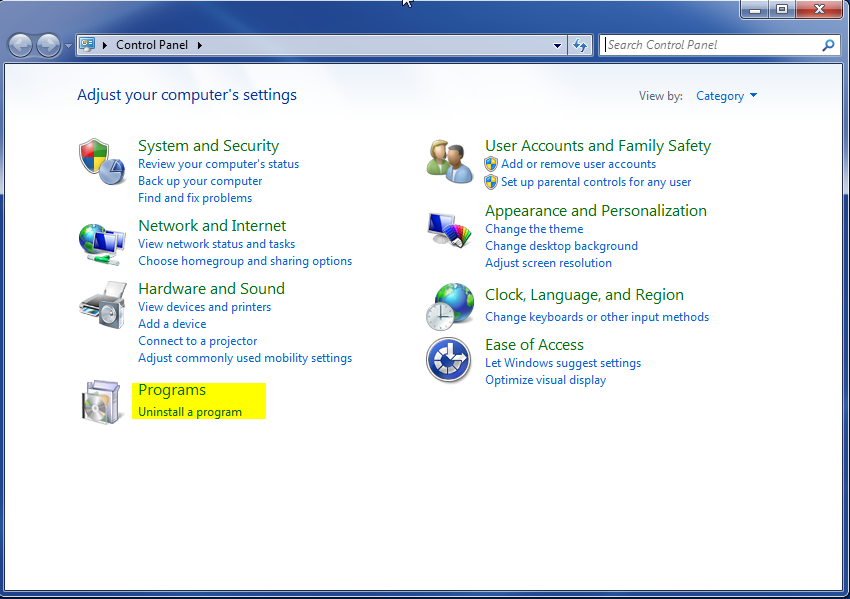
- Open up control panel by clicking on the start button in the lower left corner of your computer, and then going to Control Panel

- Once, you are in Control Panel, go to the link labeled “Uninstall a Program”. If your computer does not look like the view below, you may have to sort by categories at the top right.
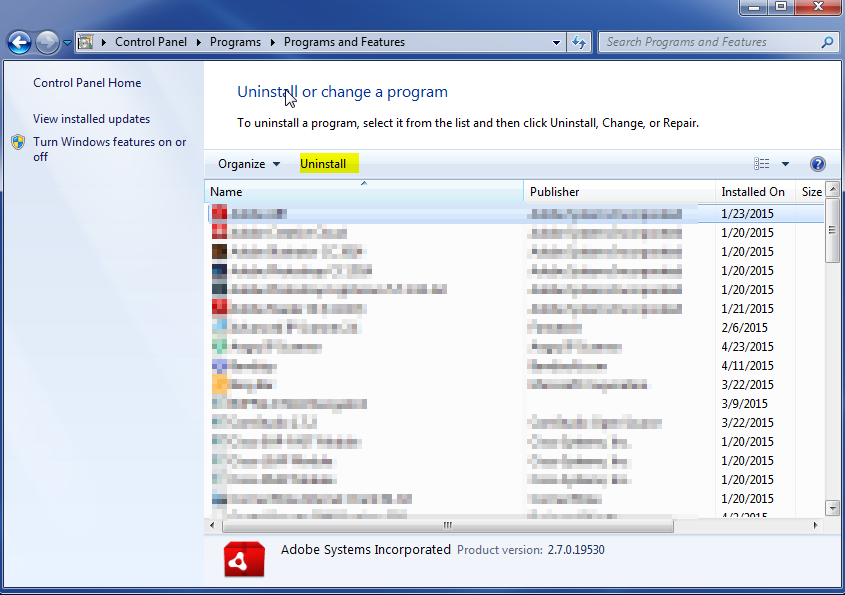
- Once in the uninstall programs section, look for the offending program. You can scroll by date installed to find programs that were installed recently. This may be a clue as to what the offending program is. Once you have found the program, highlight it and select “Uninstall” to remove
Once you have done this, you will need to go into your browser and set it to its default settings to remove the other changes it made. You will also want to scan your computer to make sure no new issues were introduced by the vulnerability. A good tool to use for this is MalwareBytes. If you already have a virus scanner, you should run this as well.
