If you have Browser Hero installed on your computer then chances are you were tricked into needing this type of software on your computer. We recommend removing it as soon as possible because it is not all it is cracked up to be. It is advertised as a free web security app that is ad supported. But, you will be slammed with many third-party ads that will make browsing a real hassle.
The software is similar to PriceHorse and Price-hips. It makes money through its pay per click model. It will show you predefined ads and will collect data about the types of ads that you click on . Therefore, it is showing you many ads, but it is also spying on your browsing habits. The things is that many of these ads are also suspect. And, it may lead you to get even more unsavory software installed on your PC.
The software can be directly downloaded from the developers website. However, you most likely got the software from it being bundled with another package. This can come with software that you downloaded from a free download site or could be inside a browser hijacker or potentially unwanted programs (PUPS).
The software will affect all popular browsers like FireFox, Chrome and Internet Explorer. The only way to be safe from all the ads is to remove the software from your system. The easiest way to remove Browser Hero is to use an automated tool like SpyWare Hunter or a similar program. I have included a link for the software below. Furthermore, if you want to do it manually, there is a link below that you can use.
How To Remove Browser Hero
- Open up control panel by clicking on the start button in the lower left corner of your computer, and then going to Control Panel
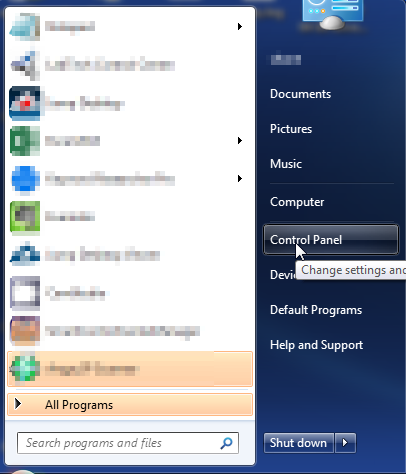
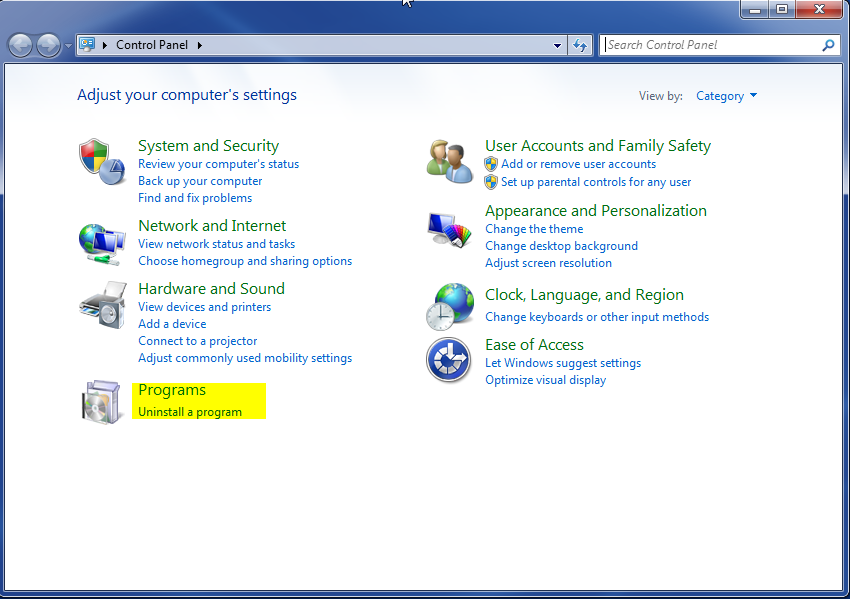
- Once, you are in Control Panel, go to the link labeled “Uninstall a Program”. If your computer does not look like the view below, you may have to sort by categories at the top right.
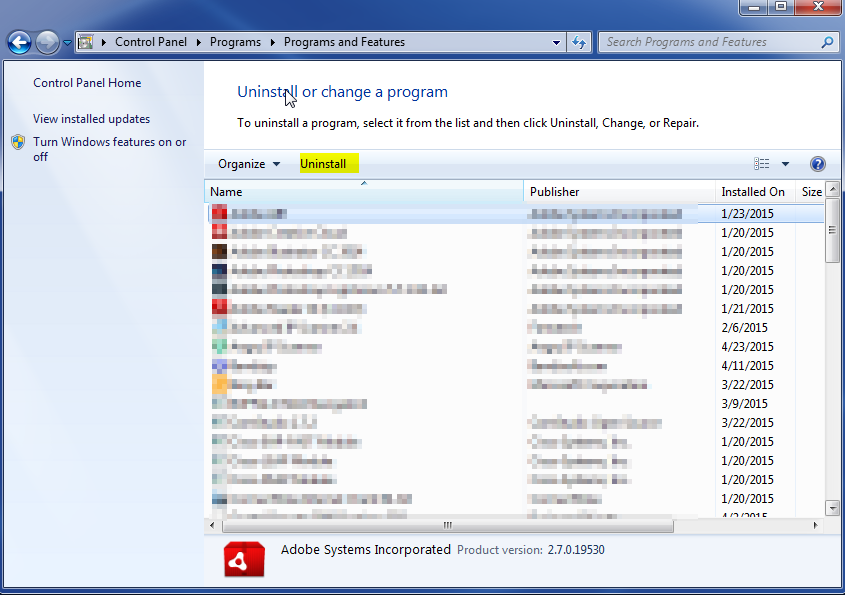
- Once in the uninstall programs section, look for the offending program. You can scroll by date installed to find programs that were installed recently. This may be a clue as to what the offending program is. Once you have found the program, highlight it and select “Uninstall” to remove
Once you have done this, you will need to go into your browser and set it to its default settings to remove the other changes it made. You will also want to scan your computer to make sure no new issues were introduced by the vulnerability. A good tool to use for this is MalwareBytes. If you already have a virus scanner, you should run this as well.
