Encapsulation
From what we’ve covered so far we can suggest that:
A class is an abstract data type made up of a combination of the relevant data and associated methods.
Each class not only has specific data members, it also has it’s member functions or methods. The methods are the tasks that the class performs, including everything from input/output to calculations to data updates. As a basic rule, if it does it to the class, it does it in the class.
This has considerable benefits. For instance, class data can be kept secure by introducing data interfaces. This is simply the provision of functions which shield the data within the class. In other words, a data member of the class can only be set, or its value retrieved, by using a specific class member function. In this way, the risk of accidentally altering a data value is hugely reduced. This extra security can in itself be a good argument for the use of an object oriented approach, but see below for the use of private and public data and methods for more on class security.
However, encapsulation also means that a class becomes highly reusable. For instance, one of the most commonly used objects in the Windows operating system is of the class window. This is simply a box with height and width values and some screen coordinates, with associated methods. This basic class has been reused countless times, by countless Windows programmers. They never need to develop this class, because it is simply provided. The only thing they need do is add their own functionality to it.
Private and Public
Class security is controlled by specifying whether data and function members are private or public. A private data member, for example, can not be read or changed by any function which is not a member of the class. Similarly, a private function can only be called by another function which is a class member.
Clearly it’s important that some class functions are public in order to allow access to the data. It’s up to the class designer how to approach this, but often the data is exclusively private, whilst most functions (methods) are public except for some internal class management functions which would be dangerous if called externally.
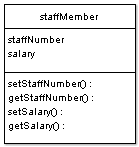
For instance, in this example class the data members staffNumber and salary are private members, so two functions have been provided for each value to perform the tasks of getting and setting the data values. This is a very common practice in an OO class, and though it can seem, sometimes, to be a little longwinded, in many cases complex operations are performed to alter a data value, and if the code to do this is included within the class, then the class becomes a transferable module that can be used as part of a class library to fit into other projects wherever it is useful.
The OO Class and the Object
It’s one thing to have a description of something and a list of all its jobs, but it’s another thing to actually have something.
Take people for example. You know what makes people. You are aware that certain variables help you to distinguish people from one another. You know what people do. But, this is all conceptual stuff. These attributes and tasks (think data and methods) are just… stuff waiting to happen. But when you actually have a person, that’s when you have an object. The object is where it all takes shape.
Think of a person versus human. There are 6 billion humans (give or take) on Earth. It could be said that each person is an instance of the class human.
Now this is important: even if there were no humans, you could still have the concept of humans, but it would not have any value. It’s each individual person that counts. Although truly unique, each person still has common traits and performs common tasks that are associated with people. In this way we can recognise even very wide variations from person to person as still being part of the group we call human.
And it’s the same with objects. The class has no real form, its a concept. It’s the objects that have form, and all the objects created of a particular class will have the class’s attributes and methods.
Class Constructors and Destructors
These are special functions which only occur at the birth and death of a class object, and are worth briefly mentioning in their own sake.
Very often a class object requires some default data values to be set at the time of its creation, or even some calculations performed, and the constructor function allows for this to be done. It is not explicitly called, but is called automatically whenever an object of a particular class is created. A simple example of what might happen in a constructor is the creation of a current timestamp. This might be so that the object has a unique identifier, or simply the current date and time is recored.
The destructor, not surprisingly, is called when the object goes out of scope and is, therefore, destroyed. The most common use of a destructor is to explicitly release any dynamically created variables in order to free RAM, an important task to prevent dangerous memory leaks.
So, after this introduction you should be able to answer:
- What is a class?
- What is a class method?
- What is an ADT?
- What is an object?
Any programming language that supports the class ADT is referred to as an object based language, but object oriented languages support more advanced techniques, which we’ll cover next. We’ll take a look at the object oriented extensions of the class system, namely inheritance and polymorphism, using a simple game as an example.