Developed by the American National Standards Institute (ANSI) standards committee in the mid-1980s – at a time when high-speed engineering workstations were beginning to tax the bandwidth of existing LANs based on Ethernet and Token Ring – the Fibre Distributed Data Interface (FDDI) specifies a 100 Mbit/s token-passing, dual-ring LAN using fibre-optic cable.
FDDI uses a dual ring topology, which is to say that it is comprised of two counter-rotating rings. During normal operation, the primary ring is used for data transmission, and the secondary ring remains idle. The primary purpose of the dual rings is to provide superiorreliability and robustness.
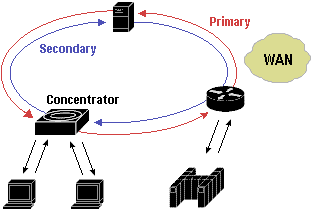
A dual-attached rooted station on the network is attached to both of these rings. This has at least two ports – an A port, where the primary ring comes in and the secondary ring goes out, and a B port where the secondary ring comes in, and the primary goes out. A station may also have a number of M ports, which are attachments for single-attached stations. Stations with at least one M port are called concentrators.
The sequence in which stations gain access to the medium is predetermined. A station generates a special signalling sequence called a Token that controls the right to transmit. This Token is continually passed around the network from one node to the next. When a station has something to send, it captures the Token, sends the information in well formatted FDDI frames, then releases the token. The header of these frames includes the address of the station(s) that will copy the frame. All nodes read the frame as it is passed around the ring to determine if they are the recipient of the frame. If they are, they extract the data, retransmitting the frame to the next station on the ring. When the frame returns to the originating station, the originating station strips the frame. The token-access control scheme thus allows all stations to share the network bandwidth in an orderly and efficient manner.
FDDI has found its niche as a reliable, high-speed backbone for mission critical and high traffic networks. It was designed to run through fibre cables, transmitting light pulses to convey information between stations. However, an implementation of FDDI protocols over twisted-pair copper wire – known as Copper Distributed Data Interface (CDDI) – has subsequently emerged to provide a 100 Mbit/s service over copper.
- OSI Model
- Network Topologies
- FDDI Networking
- Token Ring Networks
- Ethernet
- Fast Ethernet
- Gigabit Ethernet
- Peer to Peer Network Architecture
- Client/Server Architecture
- P2P Networking
- Network Hardware
- NIC Cards
- Hubs and Repeaters
- Bridges
- Routers
- Network Switches
- Network Transceivers
- Cabling
- Home Networking
- Ethernet Networks
- Phone-line Networks
- Power-line Networks
- IEEE 802.11
- Wireless Networks
- Technology Comparison