Operation and management of a dedicated server over the Internet can be achieved in several ways. Most straightforwardly, you can use control panels, provided by your hosting company, which give you easy to use interfaces for controlling the hardware and also completing common tasks on your server software.
For instance, UK hosting company Fasthosts provide a Matrix Control Panel, shown here.
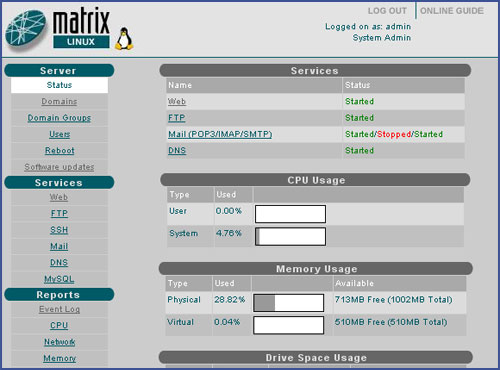
Although this is Fasthosts’ proprietary control panel system, the facilities are common to other control panel systems. From simple interfaces all web, FTP and mail services can be administered, including user and group accounts. Panels allow updates to major software, such as web server or database software, via the panel, and even reboot the machine if required.
Panels also typically provide reports on the server’s hardware status, so that CPU and memory usage can be monitored.
Control panels such as this are provided by the host companies, so there will be complete user-documentation and support provided by the host company. Clearly, these tools ease the burden of server administration, and are invaluable aids. They allow a high level access to the running of the server, taking away the need for technical know-how by providing push-button solutions and wizard style walkthroughs. However, they are always going to be limited, and it can pay to get more closely familiar with your server, and access the operating system directly.
To access an operating system remotely there are applications available that provide secure communications between computers, and allow a user on a remote computer to operate their server as if they were present. The table below shows some common methods used for this purpose. The Connecting PC column refers to the operating system running on your own home or office computer.
| Connecting PC | Server | Connection Software |
|---|---|---|
| Linux | Linux | SSH, Telnet* |
| Windows | Linux | PuTTY, WinSCP, Telnet* |
| Linux | Windows | RDC, Telnet* |
| Windows | Windows | RDC, Telnet* |
*Although almost always an option, Telnet is not advised as it is not a secure connection method.
This is not an exhaustive list, but these applications and others will give you the ability to control your server as if you were sat at that computer. You can have full operating system access, and so install and uninstall, configure and tweak the software exactly how you want it.
Next we’ll connect to our server, and start to learn about users, commands and the file system.
- Advantage to Shared Web Hosting
- Shared Hosting Issues – Shared Bandwidth and Server Resources
- The Ins and Outs of Dedicated Web Hosting
- When To Move To A Dedicated Server
- Choosing a Dedicated Server for your Website
- Managing and Operating a Dedicated Server Over the Internet Using Online Control Panels
- Accessing the Linux Operating System on Dedicated Servers with PuTTY or SSH
- How to Create a Secure Password
- Using Sudo for Super User Access to Root Privileges in Linux
- The Linux Directory Structure
- Linux Commands for Navigating and Viewing Directories
- Creating, Moving, Renaming and Copying Files and Directories in Linux
- Find, View and Delete Files and Directories Using Linux Commands
- Using vi to Edit Text Files on A Linux Dedicated Server