The GSM network can be divided into four main parts:
- The Mobile Station, which is carried by the subscriber
- The Base Station Subsystem, which controls the radio link with the Mobile Station
- The Network and Switching Subsystem, the main part of which is the Mobile services Switching Center and which performs the switching of calls between the mobile and other fixed or mobile network users, as well as management of mobile services, such as authentication
- The Operation and Support Subsystem, which oversees the proper operation and setup of the network.
The International Telecommunication Union (ITU), which manages the international allocation of radio spectrum (among other functions) allocated the bands 890-915 MHz for the uplink (mobile station to base station) and 935-960 MHz for the downlink (base station to mobile station) for mobile networks in Europe. Since this range was already being used in the early 1980s by the analogue systems of the day, the CEPT had the foresight to reserve the top 10 MHz of each band for the GSM network that was still being developed. Eventually, GSM will be allocated the entire 2×25 MHz bandwidth.
Since radio spectrum is a limited resource shared by all users, a method must be devised to divide up the bandwidth among as many users as possible. The method chosen by GSM is a combination of FDMA and TDMA. The FDMA part involves the division by frequency of the total 25 MHz bandwidth into 124 carrier frequencies of 200 kHz bandwidth. One or more carrier frequencies are then assigned to each base station. Each of these carrier frequencies is then divided in time, using a TDMA scheme, into eight time slots. One time slot is used for transmission by the mobile and one for reception. They are separated in time so that the mobile unit does not receive and transmit at the same time, a fact that simplifies the electronics.
The uniqueness of GSM technology lies in the fact that users must insert Subscriber Identity Module Cards (SIM-Cards) in their handsets. SIM Cards are small chips delivered by the GSM service provider. These SIM cards contain crucial information such as a phone number and all billing co-ordinates and can store telephone numbers. This enables users to switch GSM handsets by simply pulling out their SIM Card and inserting it into another device. As a result, users can keep the same number although they’ve switched handsets. Users can also travel to certain areas of the U.S., or countries where the GSM network uses a different frequency, hire a mobile phone, plug in their SIM Card and receive all their phone calls and SMS messages using their own usual number.
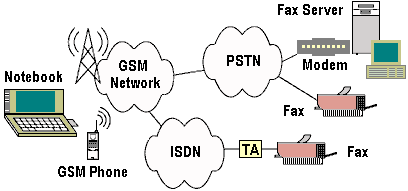
The GSM phone system used with a notebook PC and PC Card provides a comprehensive plug-and-play solution for communications on the go. Data and fax capabilities at 9600bps, along with special features like international roaming and Short Message Service (SMS) enable mobile users to connect easily and reliably when travelling from country to country. Keep in mind that data capabilities are not automatic–GSM service providers must implement this functionality for mobile users to take advantage of it. Data services can be Mobile Originated or Mobile Terminated. Mobile Originated (MO) implies that users can send data from a remote location using the GSM network. Mobile Terminated (MT) means users can receive data, faxes or SMS messages on their notebook using the GSM network.
Calls made with the second-generation GSM systems available at the end of 1999 – whether voice or data – occupied a single time slot only, offering a data rate of only 9.6 Kbit/s. In theory multiple time slots can be joined together for higher rates – in similar fashion to the aggregation of a pair of ISDN lines to double throughput. The subsequent introduction of High Speed Circuit Switched Data (HSCSD) – which required an extension to the GSM standard to introduce a new radio link protocol – allowed the use of all eight time slots to achieve data rates of up to 76.8 Kbit/s.
It was in 1993 that the first bilateral roaming agreements were established, allowing reciprocal access between foreign GSM networks. These free mobile users from concerns about the various foreign dialling tones, access codes, country codes and incompatible plugs. Once users turn on their phones and log onto the network, the system finds them. Users are able to make voice calls, collect email and receive database updates just as if they were at home.
Fax, data and SMS roaming were first introduced in 1995. SMS had originally been used to indicate that voice mail was waiting, operating in a similar manner to two-way paging. It subsequently evolved into a fully functional mobile electronic messaging system, allowing SMS messages – of up to 160 characters – to be viewed, logged, sent and received on a portable computer.
By the end of the millennium there were approaching 700 GSM mobile networks – spanning more than 100 countries across Europe, the Americas, Iceland, Asia, Africa and Australasia. Furthermore, the introduction of GSM satellite roaming had extended the service to areas where terrestrial coverage was not available. Underlying the entire system, ensuring that it functioned as a cohesive entity, were the various international roaming agreements and the Memorandum of Understanding (MoU) which defined the GSM standards and the different phases of its worldwide implementation.
However, circuit-switched data is a somewhat selfish way of using limited resources, especially when users are running bursty applications like web browsing. Packet switching, as employed on Ethernet networks and the Internet backbone, is a far more appropriate technology for allowing resources to be shared between multiple users simultaneously. Enter General Packet Radio Service (GPRS), an upgrade to GSM mobile networks that adds a packet-switched layer and is expected to deliver data rates between 21 and 100 Kbit/s. More importantly, GPRS will allow operators to charge by volume of data transferred instead of time connected. In theory, this means that users could be permanently connected to the Internet whilst mobile, but only pay for accessing email or newly requested web pages.