Not all people are in the know about the beneficial functions of Virtual Private Networks. Some users install them to unblock torrenting sites, for example, Demonoid others want to get access to the Canadian Bell content.
Yet fewer individuals are aware of fallout which might be the consequence of some VPN usage. According to TechCrunch report, it happened to Facebook Research VPN subscribers who were paid $20 monthly for installation and use of the service.
This application gets around the Apple ban on certain types of monitoring and manages to intercept personal information: private messages on social media and instant messengers, emails, search inputs, current location, and browsed pages.
That is why it is vital to choose and use a worthwhile VPN provider. We’ll highlight some points that will help you to make the right choice.
You are to find a no-log VPN provider

If you are interested in the service that would not look over your shoulder, you are to show preference to a provider which does NOT keep logs on its consumers.
It doesn’t matter how long it stores data on users: 24 hours or 3 years. At the instance of security services, the provider will have to share such information with them.
Look back on PureVPN case. On the one hand, it helped the police to find a cyber stalker. But on the other hand, it proved it DOES keep logs on user activity and shares it when it is required.
To sum up, no data – nothing to share!
Choose reliable tunneling protocols
The high-level protection when surfing the Internet would hardly be achieved without strong and reliable protocols. The most popular VPN protocols are PPTP, L2TP, OpenVPN, and SSTP. However, not all of them are equally beneficial.
Thus, PPTP safety analysis has revealed that the protocol has serious vulnerabilities. They are generally related to Authentication Header PPP, MPPE, integration between MPPE and PPP used when identifying a session key. Apart from it, PPTP offers only 128-bit ciphering.
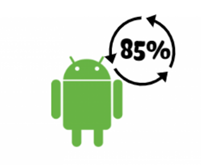
SSTP is compatible with Windows gadgets only, which make it less popular among internet users. In fact, the majority of internet surfers use Android gadgets (smartphone and tablets) – 85% of the global mobile OS market falls for the share of Android.
The most secure and reliable VPN protocols are OpenVPN and L2TP/IPsec. OpenVPN represents open source technology that works through firewalls and provides first-class security. L2TP in combination with IPsec is as secure as OpenVPN but does not require any additional soft to install.
Reckon with VPN location
The place where a VPN is registered is of great importance. Given that a VPN provider is registered in one of the countries which hold membership of a ‘14 eyes’ alliance, user privacy might be under threat.
It is recommended to show preference to the services which are registered in places like the British Virgin Islands or Cyprus, for example.
Horrifying facts in 2018
Although security experts work to the bone to invent top-notch security tools, hackers become more resourceful. The events of 2018 prove it:
- an average cost of cyber breach increased by 4.8% (equals $141-148);
- the number of identity theft victims in the US raised by 8% in 2018;
- 4 in 5 files stored online are protected, others are publicly available;
- 1 in 3 phishing emails is opened by the US residents;
- 34% of Americans fell victims to data breach;
- about 230 thousand malicious software samples appear daily.

Virtual Private Networks serve to prevent such troubles. They provide subscribers with internet privacy, security and anonymity.
Conclusion
Well, let us sum up.
How can a VPN help users in 2019?
First and foremost, a reliable provider guarantees private information interchange.
Second, no-logging policy prevents the disclosure of information to third parties.
Third, advantageous VPN location serves to get rid of monitoring.
Fourthly, a credible service stave off data breaches, phishing and other forms of hacking attacks.
As a bonus, one gets access to all content on the Internet, fast speed, and anonymity.
Some VPN providers allow testing their services free of charge for a limited period of time. We find it rather beneficial, as we don’t have to pay for a pig in a poke.
Be safe online and keep on reading pctechguide!