
PROS: The Eset Nod 32 Anti-virus 4 program is a great alternative to well known software. It assists computer systems in detoxing and protects users from malicious programs.
CONS: Eset Nod 32 Anti-Virus protects personal computer users from phishing attacks as well as harmful programs that can cause damage to systems.
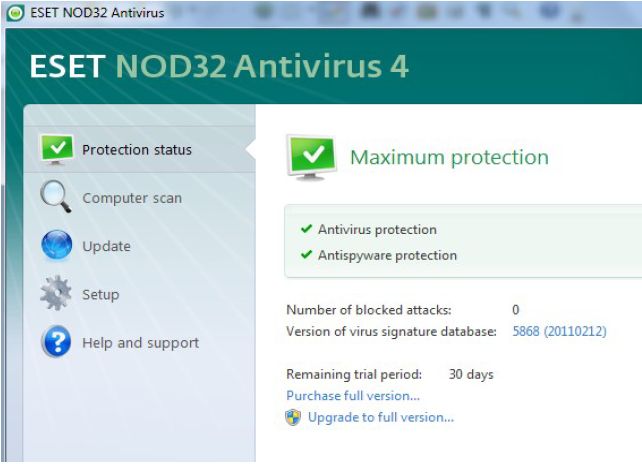
OVERVIEW: Good protection for computers from online threats. The interface is easy to use, follow and understand.
Eset Nod 32 Anti-virus Review
Company:http:// www.eset.com
Version: 4.2.71.2
Rating: 10 out of 10
Release Date: January 21, 2011
Operating Systems: Windows XP, Vista, Windows 7, NT 4.0 with service pack 6. Apple OS X
Price: $39.95
What It Does:
Antivirus, spyware, trojan, adware, hacker and phishing protection for personal computers. Macintosh supported. External storage support (usb).
Product Details:
Antivirus protection is a key software tool in keeping a computer system functioning well. With thousands of online threats received via innocent emails from friends and family as well as malicious websites which house other invisible but deadly attackers, an antivirus program should be the first software installed before operating any new computer. It may be difficult to chose from numerous products on the market, but among well know alternatives, ESET Nod is a strong contender. The product is available for Windows 32 (XP, Vista and Win 7) and 64bit.
Interface is in a simple, clean layout with clearly marked option and a limited number of menu choices.
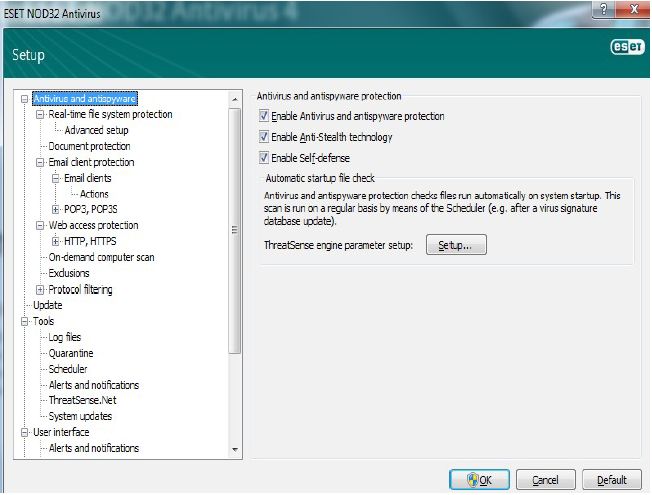
Scan choices are Smart Scan and Custom, allowing the end user to select which drives and folders are to be targeted for cleansing. Upon completion, a report can be viewed on the screen with an accompanying log. The log contains all errors, warnings, critical warnings, informative and diagnostic records. The log can also be exported.
Given virus files can be transported to other machines when an external USB drive, protecting this storage locations is just as important as you main storage. ESET Nod 32 will automatically sense the external drive and quickly determine the existence of all malware. There have been some reports in tech forums about a year ago that ESET had problems with Vista’s service pack 2’s corruption of NOD32, Eset’s virus engine. This same issue occurred Windows Server 2008. Response from the company was limited and a solid eta was not provided. However, ESET delivered a patch to resolve the incompatibility issue and the software continues to receive superior scores against other antivirus leaders like Norton, Kapersky, Trend Micro and McAfee.
ESET provides a number of advantages to the end user. The main purpose of an antivirus program is to catch the culprits. ESET has been tested by independent testing labs as the product that detects the largest number of viruses. Also, this product has a lesser number of false positives, a faster boot time and a smaller resident memory requirement. In April of 2010, ESET received the VB100 award, given malware porgrams in terms of their effectiveness after a set of testing requirements. Another testing organization, antivirusware.com also gave ESET Nod high their “Most Friendly Award” for it’s simplicity of operations for any user.
Many antivirus program contain a service that proactively checks suspect files and will report them back to the manufacturer if they “appear” to be a threat for which there may be a need to watch the file closely, and take immediate action upon a critical issue. Even in this area ESET’s Nod 32 tops the charts.
Security:ESET Nod prompts the user to enter a username and password during the setup process. Hidden trojans may allow background activity (ex. Login) unknown to the user. This I password and user login provides a security measure in the event system settings are accessed by an intruder, they can not be altered. Additionally the software will run behind a proxy server for those with networks in play. The password is also required upon uninstalling the program from your system.
Installation: Using an .msi file the software installs quickly and easily. I chose the custom install to view what additional choices are presented during the install process. A custom install will also allow you to set a proxy server, select specific locations to scan and other advanced settings.
Knowledge Level
Novice = 3 Intermediate = 2 Expert = 1
Software operations is fairly easy. The wizards ensure you take all the steps in order for the synchronization to be completed.
Technical Support: Set provides a web based knowledge base which includes numerous videos on product activation, installation, and virus remediation. If the issue isn’t urgent, there is a provision to submit an online support request that is stated to be returned within 1 business day. There is no phone support.
License Model: A single PC license is $39.95 for 1 year.
2 Systems: $55.99
3 Systems: $71.99
4 Systems: $95.99
However you can add protection for 2 years as follows:
1 System: $58.99
2 Systems: $82.99
3 Systems: $106.99
4 Systems: $143.99
The software can also be purchased for small businesses, starting with a 5 pack and will support the Microsoft Exchange email server.
Extras
ThreatSense.net is built into the application. This feature will send an alert to the software owner of any viruses that are being detected across the web world, and also suspected from the end user PC to ESET’S labs for detox.
Conclusion This software is very easy to use and well rated. ESET Nod Antivirus may have a strange name but in the odd world of viruses, there’s nothing more strange than a antivirus program that offers little protection. ESET Nod offers you strong protection, perpetual guard duty against millions of electronic pest.


Thank you so much for keeping us all informed on topics of such great importance. I am particularly interested in the subject of mold