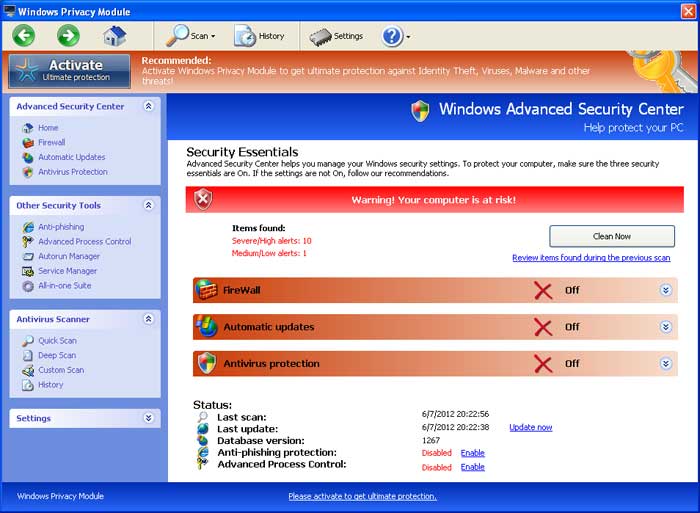
Windows Privacy Module
Welcome! If you’ve found your way here, it probably means that you’ve gotten infected with Windows Privacy Module. Windows Privacy Module is another one of the delightful fake antivirus infection variants. Each of these infections can go by a variety of names. The aim of an infection of this nature is to convince the user that the only way to remove the “infections” it finds on your computer is to purchase the software. Not only is this not the case, but purchasing the software would release your credit card information to some, rather obviously, less than reputable individuals. The infection does this by making it difficult to open any programs you might use to remove it, as well as blocking the user from using the internet to find removal guides and software. It can also alter your browser’s search settings, making this task doubly difficult. This client is a clone of Anti-Spyware, XP Home Security 2012, XP Anti-Virus 2012 and XP Security 2012 as well as Win 7 Anti-Spyware, Win 7 Home Security 2012
How Did I get infected with Windows Privacy Module?
Generally infections of this nature get into your computer by being imbedded within a video, an mp3, or flash based ads on a webpage. Normally, the administrators of the website aren’t even aware that the infection has become embedded in their website.
How Much Damage is Windows Privacy Module Doing?
The most obnoxious thing about infections of this nature is that they block any .exe file from running. This basically means that it will block almost any program installed on your computer from launching, be it task manager, internet explorer, or Microsoft Word. Just because you can run executables doesn’t necessarily mean that your computer hasn’t been a victim of this infection, simply that it hasn’t had the time to cause this problem yet. Once this does occur, it can make using your computer, and removing the infection, very difficult. However, if you continue reading, we’ll give you a step-by-step walkthrough for removal of Windows Privacy Module.
Windows Privacy Module
» Download
Windows Privacy Module Removal Software
How to Remove Windows Privacy Module?
This article will cover three main techniques for removing Windows Privacy Module.
1. Use Anti-virus software (Note you may need to follow the manual guide to start so you can install a client.)
2. Hire an expert ( We Recommend http://www.pcninja.com. This is a remote computer repair company)
3. Remove this threat yourself following our manual removal guide.
Automatic Windows Privacy Module Removal
Online Windows Privacy Module Removal Service
Windows Privacy Module Manual Removal Procedures
Step 1. If you are unable to run any executable programs at all this may be from the virus changing your registry settings. If this is the case you may need to use this patch. It is only for Windows 7 computers. Download Win 7 Fix exe Issue here.
Step 2. You need to stop and delete the main .exe file that is running Windows Privacy Module.
You should be able to locate this file at
- %AppData%\Protector-[random 3 chars].exe
- Exmaple: Protector-1t4.exe
Keep in mind that the USERNAME will be your user name
The file is called Protector-[random 3 chars].exe. Expect this name to change over time.
Once you locate the file you will need to re-name the file. To do this you can right click on the file named and select “Re-name”. Name it whatever you want. Once done re-start your computer. Next time you boot up the virus should not be running. Now you should be able to delete the file name.
At this time you should run a full virus scan. We Recommend Spyware Doctor with Antivirus. However you can use any client you trust the most. To see a list of other clients we recommend check out our Anti-virus Reviews section.
Windows Privacy Module Registry Removal Procedures
We don’t recommend that the user go into the registry and attempt to edit it manually. Besides the .exe file extensions being disassociated, for which we’ve posted a pre-configured fix, there isn’t anything the user would need to edit in
the registry anyway. Any decent antivirus client should be able to fix any registry problems that may linger following removal of the infected .exe file. You may also want to use a registry cleaner like PC Health Advisor Here to clean out the registry and scan for other malware. You can also read all or registry cleaner reviews
Windows Privacy Module Directories:
Windows 7 / Windows Vista
- %AppData%
%AppData% is a home directory listing that will take you directly to the users Application Data directory. This should be checked on each users account that is affected by the infection.
If you require advanced help or just want an expert to remove the virus than use this computer repair service. The charge is under a hundred bucks and they can often get started right away. These are real experts when it comes to malware and virus removal.
Related Article Keywords: Windows Privacy Module, Remove Windows Privacy Module, Windows Privacy Module Removal, How to Remove Windows Privacy Module