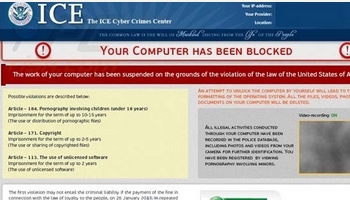
ICE Cyber Crimes Center warning is not from ICE the United States government agency. This is an extortion scam that is a clone of another virus called FBI Money PAK.
If you would like to confirm this just look at http://www.ice.gov/news/releases/1302/130215washingtondc2.htm
They made a press release over this threat. I think it’s great they actually sent something out about it. I did not recall the FBI stepping forward with a Press Release when someone used their name in a scam. Perhaps they did and I just could not find it.
The Real ICE press release really does not offer much help to people. They say to report it via the phone at 866-347-2423. You are welcome to do so but don’t expect them to say much except OK and we are aware of the virus threat.
The other advice they offer is
- Keep operating systems and legitimate antivirus and antispyware software updated.
- Contact a reputable computer expert to assist with removing the malware.
Both of these things I can strongly agree with. I know people love free antivirus clients but in this world free does not cut it. Those free versions all have paid versions. The paid versions are always up to date and offer more security then the free versions.
As for keeping your operating system up to date, you should have Windows automatic updates turned on already. To double check just type the word update in the Windows search bar and then select “Windows Update”. It will ask you to turn it on if it’s not on already. You also need to keep your web browser like Internet Explorer, Firefox and Chrome up to date. That and java. Those are the most important programs to keep up to date to help fend of exploits.
As far as finding a good computer repair company goes, we have been recommending out http://www.pcninja.com for several years. This U.S. based remote computer repair company knows what the hell they are doing and can fully remove the ICE Cyber Crimes Center Virus.
ICE Cyber Crimes Center
» Download ICE Cyber Crimes Center Removal Software
Automatic ICE Cyber Crimes Center Removal
Online ICE Cyber Crimes Center Removal Service
ICE Cyber Crimes Center Manual Removal Procedures
We do not recommend manual removal but you can still do it.
To start you need to kill off the main program that is “Ice Cyber Crimes”. This is one single executable file that has to be disabled. After that you can run a full virus scan to ensure there are no other traces.
- [random].exe ( Example is woo0.exe ) Your file trace will be named different. Every infection will have a different name. However the file tends to hide in the same location
Some Tips on Locating the file.
Known File Paths. To view these file paths you will need to either manually type them in or show hidden files and folders. Learn how to at http://www.removevirus.org/show-hidden-files-and-folders
Windows XP:
- C:\Documents and Settings\USER NAME\Local Settings\Application Data
Windows Vista/ Windows 7/ Windows 8:
- C:UsersUSER NAMEAppData\Local
- C:UsersUSER NAMEAppData
A. Browse to the file location shown above under File Locations and re-name the file first and then restart your computer. Then browse to that file location again and delete the file. You can not delete a file while it is in use.
While you may not know the exact name of the file here are a few tips to locate it.
A1. The file will not be named something that makes sense, it will be jumbled like 3248jf.exe or 24055jndd.exe.
A2. You can sort the file by date in the folder and see which ones have been installed in the last few days. In most cases you will only have 1-3 files that match the time of your infection. From there it should be easy to see which one is the one you need to re-name.
B. Boot into Safe Mode with networking and download an Antivirus client and run a full scan. We like Spyware Doctor with Antivirus. You will be able to install it and run the virus scan. Learn how to boot into safe mode here
C: Log-into another users account and see if you can delete the file. Again use the File Locations below to locate the file
E: Start the Task Manager the very second you login and terminate the process that way.
After you have killed off the file you have to run a full virus scan. We already mentioned which AV client we like to use. You can use another if you like. Just be sure to run a full scan. This is to ensure you have everything and no other threats are present on the computer.
As mentioned already, we also like http://www.pcninja.com. This computer repair company can remote into your PC and fully remove all virus threats found on the system. They do a great job and based in California.