The InboxNow toolbar is another browser plugin that promises lots of useful features, but all it gives you is a bunch of headaches.
If you have noticed this toolbar in your browser it is recommended to remove it as soon as possible. It will attach itself to all the major web browsers like Internet Explorer, Google Chrome and Mozilla Firefox. The plugin is not to be trusted. This is another toolbar that is put out by MIndspark Interactive Network, Inc. Anything you get from them should be treated as suspect. The best defense from these kinds of tools is to have a reputable virus scanning software on your computer. Even better, it is a good idea to not install software from third-party websites.
This toolbar will change the homepage and default search engine to Ask.com. During installation you are given the chance to block these changes. But, most people do not read this or skip over it.
You can remove the InBoxNow Toolbar from your system by following the manual steps we have outlined below. It is not too difficult to do, but does require a bit of computer knowledge. However, if you want something that is more automated, then we recommend using SpyHunter. You can get a free copy by clicking on the link below.
iStartSurf is typically installed in bundled software. Many times it is bundled in video recording software, download manager and PDF creators. Unfortunately, even if you find out what it was bundled with and uninstall it, it will not remove the iStartSurf malware. Therefore, it is best to follow the directions below to help remove the program from your system.
Uninstall InBoxNow Toolbar from Windows.
- Open up control panel by clicking on the start button in the lower left corner of your computer, and then going to Control Panel
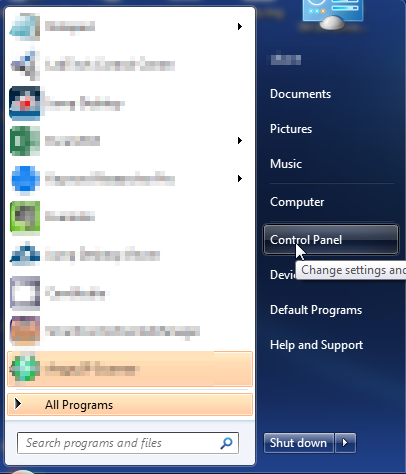
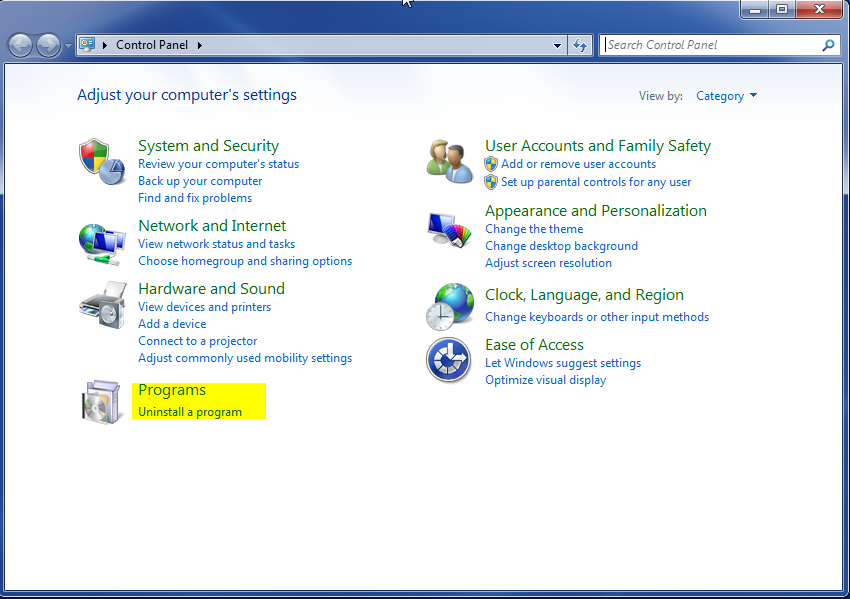
- Once, you are in Control Panel, go to the link labeled “Uninstall a Program”. If your computer does not look like the view below, you may have to sort by categories at the top right.
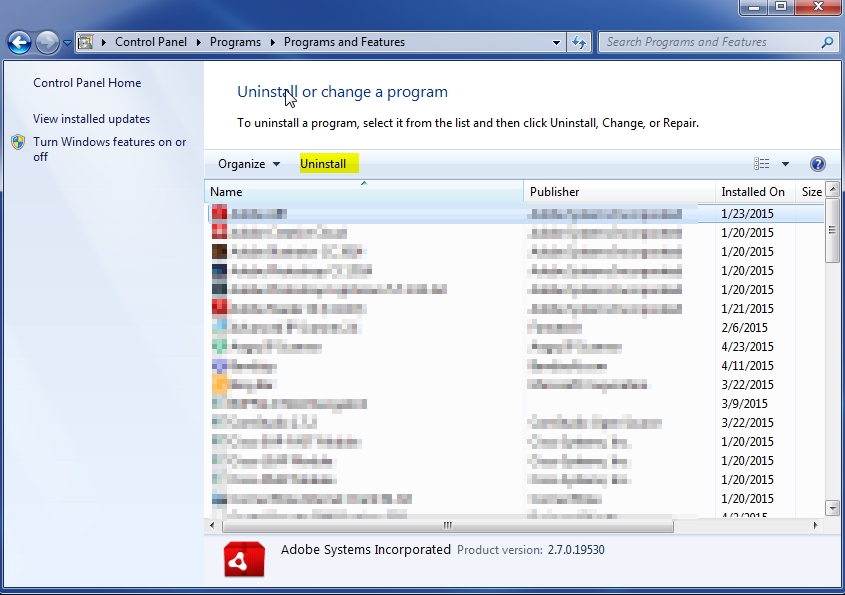
- Once in the uninstall programs section, look for the offending program. You can scroll by date installed to find programs that were installed recently. This may be a clue as to what the offending program is. Once you have found the program, highlight it and select “Uninstall” to remove
Once you have done this, you will need to go into your browser and set it to its default settings to remove the other changes it made. You will also want to scan your computer to make sure no new issues were introduced by the vulnerability. A good tool to use for this is MalwareBytes. If you already have a virus scanner, you should run this as well.
