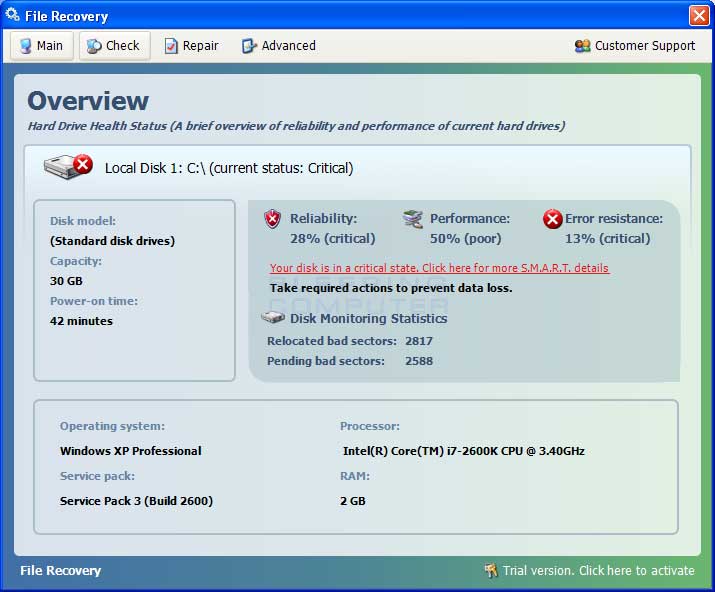
File Recovery
Welcome! If you’ve made your way to this page, you’ve likely been infected with File Recovery. Infections of this kind are generally termed scareware, they attempt to force the user into paying for them by making the case that you’re experiencing hardware failure, in this instance, by saying that the user’s hard drive is failing. Malware of this kind accomplishes this by making your computer more difficult to use while simultaneously throwing up scary error messages indicating the aforementioned hardware issues. They may also alter your browser’s search settings making finding help particularly difficult. But never fear, pctechguide is here! This client is a clone of Anti-Spyware, XP Home Security 2012, XP Anti-Virus 2012 and XP Security 2012 as well as Win 7 Anti-Spyware, Win 7 Home Security 2012
How Did I get infected with File Recovery?
Infections of this type usually come from infected webpages, meaning that you may have visited a site that inserted the malicious code in the course of loading its pages. In all likelihood, you won’t even be asked to install the software, it just shows up on your computer suddenly with no interaction from the user. If this is the case, you should consider upgrading to a better anti-virus solution.
How Much Damage is File Recovery Doing?
With most infections of this type, the only real damaged caused is what the infection does immediately to make your computer more difficult to use, disassociating executable files and altering your browser search settings. The disassociation of executable files is the cause of the message you’re getting asking what to use to open any program that you try to run. This is simply because the registry information that tells Windows how to execute executables has been damaged. We’ve posted a quick fix for this below in the guide.
File Recovery
»Download File Recovery Removal Software
How to Remove File Recovery?
This article will cover the three major means to remove this infection: 1. Use Anti-virus software (Note you may need to follow the manual guide to start so you can install a client.) 2. Hire an expert ( We Recommend http://www.pcninja.com. This is a remote computer repair company) 3. Remove this threat yourself following our manual removal guide.
Automatic File Recovery Removal
Online File Recovery Removal Service
File Recovery Manual Removal Procedures
Step 1. If you are unable to run any executable programs at all this may be from the virus changing your registry settings. If this is the case you may need to use this patch. It is only for Windows 7 computers. Download Win 7 Fix exe Issue here.
Step 2. You need to stop and delete the main .exe file that is running Windows Control Series. You should be able to locate this file at
-
<Totallyr andom>.exe.exe
- Exmaple: dfasdtrfe453453.exe
Keep in mind that the USERNAME will be your user name The file is called . Expect this name to change over time. Once you locate the file you will need to re-name the file. To do this you can right click on the file named and select “Re-name”. Name it whatever you want. Once done re-start your computer. Next time you boot up the virus should not be running. Now you should be able to delete the file name. At this time you should run a full virus scan. We Recommend Spyware Doctor with Antivirus. However you can use any client you trust the most. To see a list of other clients we recommend check out our Anti-virus Reviews section.
File RecoveryRegistry Removal Procedures
We don’t recommend that users manually edit the registry. Aside from the issue this infection causes with executable files, there shouldn’t be any damage to the registry that cannot be solved automatically by a good antivirus program and registry cleaning software. You may want to use a registry cleaner like PC Health Advisor Here to clean out the registry and scan for other malware. You can also read all or registry cleaner reviews
File RecoveryDirectories:
Windows 7 / Windows Vista
- %CommonAppData%\<Totally random>
- %CommonAppData%\<Totallyr andom>.exe
- %CommonAppData%\~<Totally random>
- %CommonAppData%\~<Totally random>
- %StartMenu%\Programs\File Recovery\
- %StartMenu%\Programs\File Recovery\File Recovery.lnk
- %StartMenu%\Programs\File Recovery\Uninstall File Recovery.lnk
- %Temp%\smtmp\
- %Temp%\smtmp\1
- %Temp%\smtmp\2
- %Temp%\smtmp\3
- %Temp%\smtmp\4
- %UserProfile%\Desktop\File Recovery.lnk
%AppData% is a home directory listing that will take you directly to the users Application Data directory. This should be checked on each users account that is affected by the infection.
If you require advanced help or just want an expert to remove the virus than use this computer repair service. The charge is under a hundred bucks and they can often get started right away. These are real experts when it comes to
malware and virus removal. Related Article Keywords: File Recovery, Remove File Recovery, File Recovery Removal, How to Remove File Recovery