The whole premise of FusionPlayer is that it will let you create media play lists using videos on the computer and videos from the Internet. That is its hook and the incentive to install the program. The truth is, however, this is a PUP (potentially unwanted program)that is nothing more than a useless piece of software that will provide nothing more than headaches and unwanted ads. The software will show you a ton of ads, but also change your search provider. The best thing is to avoid installing FusionPlayer all together. But, if you find that it is already installed, this guide will provide tips on how to remove it from your computer.
Information about the software can be obtained from fusionplayer.com. But, the site does not actually contain any installation software. Its most favored form of distribution is to be bundled with other forms of malware. That means if you find FusionPlayer on your system there is a good bet that there are other forms of malware on you computer. Therefore, it is a good idea to install a malware scanner to see if you can catch the other issues on your machine.
FusionPlayer does not actually work the way it is advertised. Many have found that it does not actually play media files. That means its sole purpose of creation was not to provide a service. Instead it is meant to display ads and collect information from your browsing habits. And, many of the ads are for sites and services that are not that legitimate.
This means that if you do see ads from FusionPlayer, you should ignore them until you remove the software. Do not sign up for any services that are recommended by the ads. It will just cause more problems and headaches for you. There is a good chance that the ads will lead you to even more spyware and adware. And, that means even more computer cleanup.
The removal process of FusionPlayer is not too difficult, but care should be taken. If you do not do it correctly, you will be under the false assumption that the software was removed when it still continues to run. If you would like an easier way to remove the software, we recommend using SpyHunter to remove it. This is a piece of software that will scan your computer for free and report any problems. You can find the program by clicking on the link below.
Uninstall Fusion Player from Windows.
- Open up control panel by clicking on the start button in the lower left corner of your computer, and then going to Control Panel
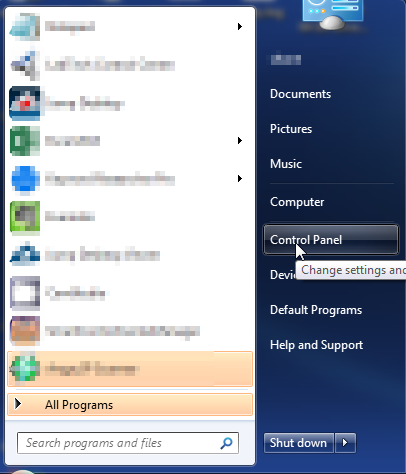
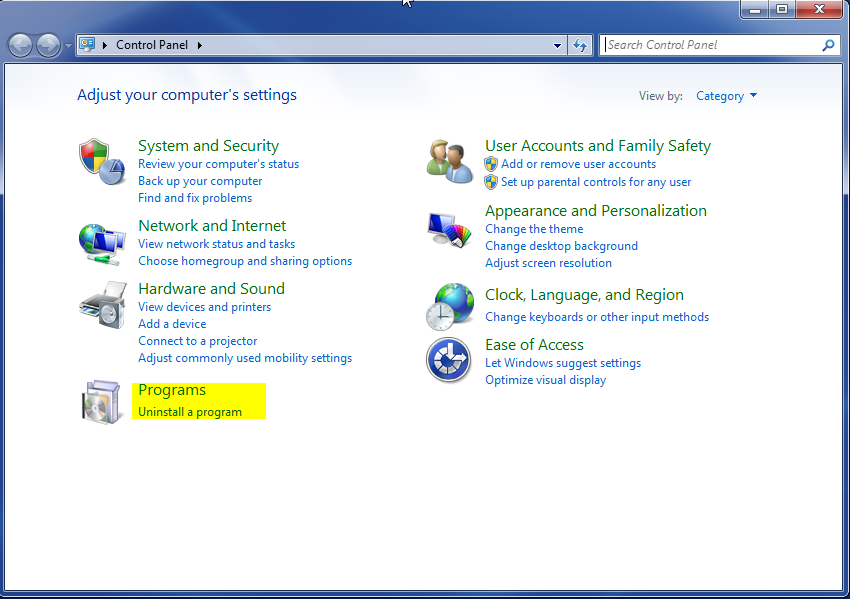
- Once, you are in Control Panel, go to the link labeled “Uninstall a Program”. If your computer does not look like the view below, you may have to sort by categories at the top right.
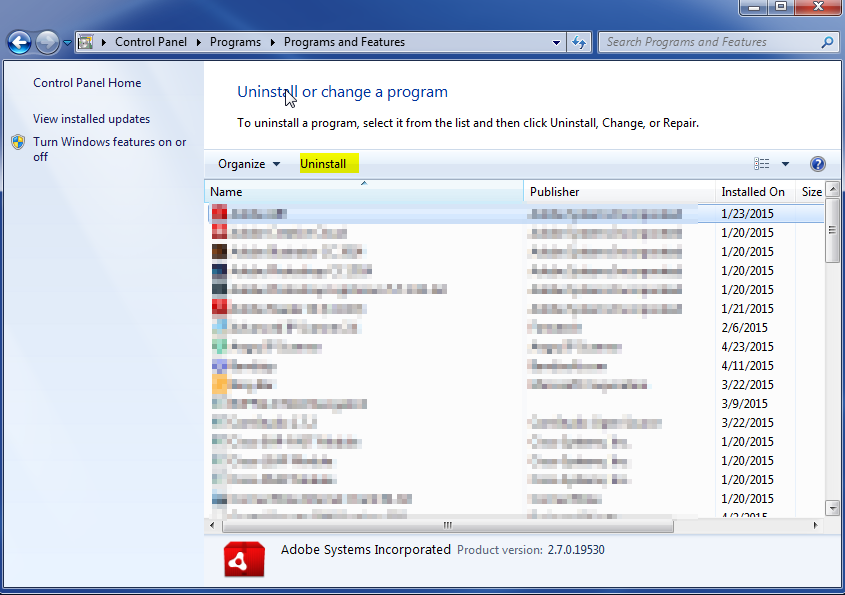
- Once in the uninstall programs section, look for the offending program. You can scroll by date installed to find programs that were installed recently. This may be a clue as to what the offending program is. Once you have found the program, highlight it and select “Uninstall” to remove
Once you have done this, you will need to go into your browser and set it to its default settings to remove the other changes it made. You will also want to scan your computer to make sure no new issues were introduced by the vulnerability. A good tool to use for this is MalwareBytes. If you already have a virus scanner, you should run this as well.

