ArcadeHall is a game downloader. Its catch is that it promises users the ability to play online games without the need to download the files. With the popularity of games, it is a good bet that there are many people downloading this application. The application is hosted at a website called arcadehall.com. But, it more than likely uses bundling tricks to get itself installed on your machine. That alone makes it a worthy candidate for removal from your computer ASAP.
It is no surprise that once the software is installed you will start seeing various ads and commercials while browsing on the Internet. These ads can slow down your PC and become a pain while browsing. But, some of the ads that are served can be potential avenues to get further infections from other suspect software. The promise of free video games is not worth the grief all this will cause you.
The good news is that ArcadeHall is not a serious threat to your system by itself. And, removing the software is pretty easy. We have included the directions to remove it below. But, if you want a simple, automated way to remove it then you really should consider using SpyWare Hunter to remove it. This is a free tool that will identify any issues you have on your computer. If you do need to remove anything with it, then you will have to purchase it. But, then you can use it to protect your machine from any future issues. If you are interested, just click on the orange button below.
iStartSurf is typically installed in bundled software. Many times it is bundled in video recording software, download manager and PDF creators. Unfortunately, even if you find out what it was bundled with and uninstall it, it will not remove the iStartSurf malware. Therefore, it is best to follow the directions below to help remove the program from your system.
Uninstall ArcadeHall from Windows.
- Open up control panel by clicking on the start button in the lower left corner of your computer, and then going to Control Panel
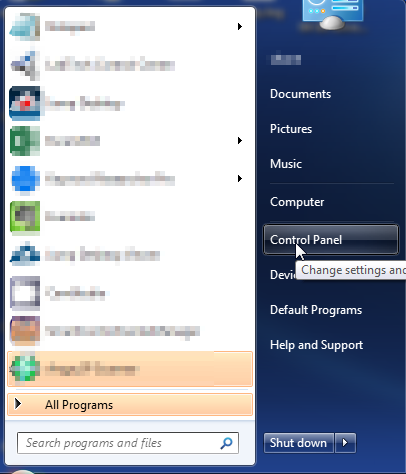
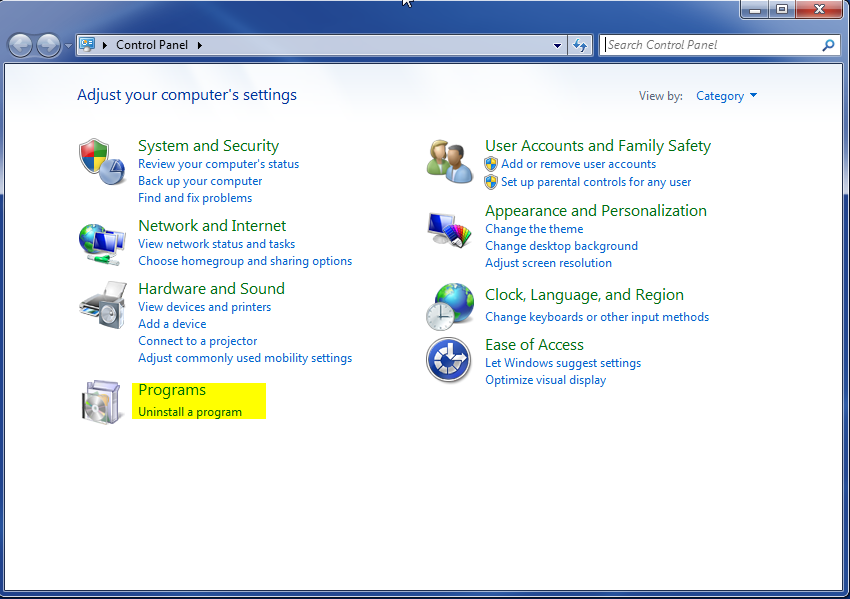
- Once, you are in Control Panel, go to the link labeled “Uninstall a Program”. If your computer does not look like the view below, you may have to sort by categories at the top right.
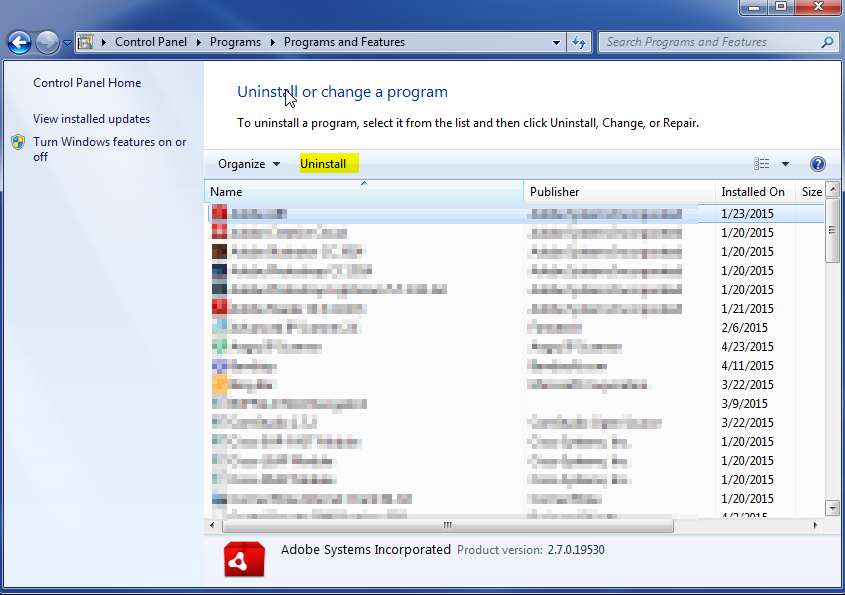
- Once in the uninstall programs section, look for the offending program. You can scroll by date installed to find programs that were installed recently. This may be a clue as to what the offending program is. Once you have found the program, highlight it and select “Uninstall” to remove
Once you have done this, you will need to go into your browser and set it to its default settings to remove the other changes it made. You will also want to scan your computer to make sure no new issues were introduced by the vulnerability. A good tool to use for this is MalwareBytes. If you already have a virus scanner, you should run this as well.
