Before mounting the device, you’ll need to configure it via the jumper switch located on the rear of the drive.
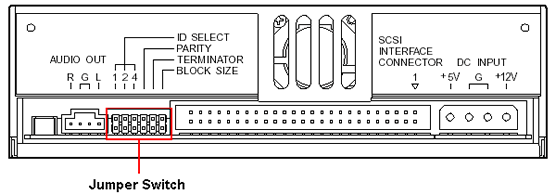
SCSI ID setting:
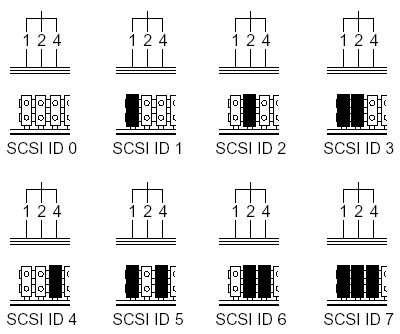
The three leftmost jumpers are used to configure the drive’s SCSI ID number. This can be assigned a value of 0 through 7.
Usually, 7 is reserved for the SCSI host adapter card and 0 is reserved for a SCSI-based C: hard disk drive.
In this case the associated User Guide directs use of a number between 1 and 6, and advises that the factory setting is 3.
Each peripheral attached to a SCSI-2 host adapter card, as well as the card itself, must be assigned a unique SCSI ID number from 0 to 15 (0 to 7 for SCSI-1). A SCSI ID uniquely identifies each SCSI device on the SCSI bus and determines priority when two or more devices are trying to use the SCSI bus at the same time.
Each device on the chain, including the host, must be identified by a unique ID number. One SCSI device must not use the same ID number as another, but they may be numbered non-sequentially. Most SCSI host adapters feature external and internal connectors, with the option for the chain to extend in either or both directions. There’s no relationship between the IDs and the physical position on the bus, but both ends must be electrically terminated with resistors to prevent signal reflections and guarantee data integrity over long cable lengths. Termination comes in several varieties, from physical jumpers or plugs to software configurations.
Here are some general guidelines for SCSI IDs:
- For internal SCSI peripherals, the SCSI ID usually is set by configuring a jumper on the peripheral.
- For external SCSI peripherals, the SCSI ID usually is set with a switch on the back of the peripheral.
- SCSI ID numbers don’t have to be sequential, as long as the SCSI host adapter card and each peripheral has a different number. For example, you can have an internal SCSI peripheral with ID 0, and an external SCSI peripheral with ID 6. Gaps in the sequence of numbers don’t matter.
- SCSI ID 7 has the highest priority on the SCSI bus. The priority of the remaining IDs, in descending order, is 6 to 0, 15 to 8.
- SCSI host adapter cards are normally preset to SCSI ID 7 and should not be changed. This gives it the highest priority on the SCSI bus.
- Most internal SCSI hard disk drives come from the factory preset to SCSI ID 0.
- If you have 8-bit SCSI peripherals, they must use SCSI IDs 0, 1, 2, 3, 4, 5, or 6. SCSI ID 0 is recommended for the first SCSI hard disk drive.
Parity setting:
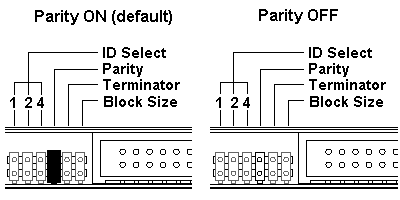
- Parity ON (with a jumper)
– Parity check will be performed.
- Parity OFF (without a jumper)
– Parity check will not be performed.
Terminator setting:
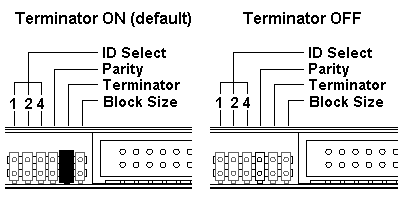
The terminator setting indicates whether or not a device is the last in the chain:
- Terminator ON (with a jumper)
– Use this setting if the CD-ReWriter is the last device in the internal SCSI daisy-chain.
- Terminator OFF (without a jumper)
– Use this setting if there are other devices in the internal SCSI daisy chain after the CD-ReWriter.
Block Size setting:
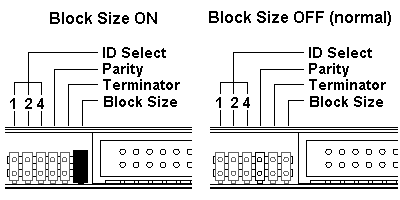
- Block Size ON (with a jumper)
– Block Size is set to 512Byte/sector. Typically used for UNIX workstations.
- Block Size OFF (without a jumper)
– The normal setting for Windows PCs.