Squeeze either side of the connector to connect the supplied SCSI cable to the SCSI host adapter card’s external SCSI connector.

Connect the other end to the scanner’s 50-pin DB50 connector …
… and plug in the power adapter power cord

The proliferation of SCSI standard versions over the years has led to a situation in which there exist many different types of SCSI cables and connectors. Whilst each new version of SCSI is backwards compatible, it can require a bewildering array of cables, connectors and adapters to connect together a bunch of SCSI peripherals that spans multiple variants of the standard:
| Host or Host Adapter | Connector |
|---|---|
| 50-pin Centronics:
Most SCSI SLOW (5 MBps) computers and host adapters use the Centronics-type 50-pin connector. Also some 8-bit Fast computers and host adapters. |
 |
| DB25:
Apple/Mac and some older Sun 8-bit workstations. |
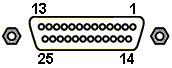 |
| DB50:
Old Sun and DG Computers, Zip drives and many scanners. |
|
| HD50:
Many 8-bit SCSI FAST (up to 10 MBps) computers and host adapters use this 50-pin High-Density connector. |
 |
| HD68:
All FAST/WIDE (16-bit) SCSI-3 computers and host adapters plus old DEC single-ended SCSI use this 68-pin High Density connector. |
 |
| SCA80:
New Single Connector Attachment 80-pin connector used for Ultra2Wide/LVD, Ultra160 and Ultra32O applications |
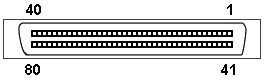 |
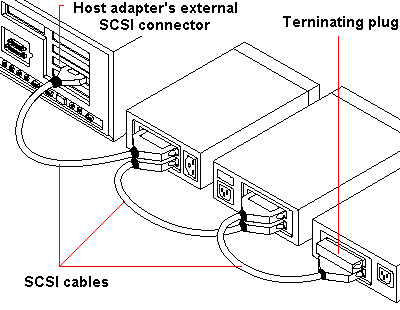
It’s possible to connect a number of SCSI devices by creating a daisy-chain, that is, plugging one device into the next.

The last device in the chain needs to terminated.
In this case, since it’s going to be the only external SCSI device, the SCSI terminator the scanner was supplied should be left in place.
To ensure reliable communication on the SCSI bus, the end of the chain of devices on the SCSI bus must be properly terminated with resistors to prevent signal reflections and guarantee data integrity over long cable lengths.
In fact, there may be one or two chains. One is the external chain from the external port on the SCSI adapter card, the other is the internal chain, connected from the card’s internal SCSI connector. Termination is accomplished by the peripheral at the end of each cable – or the end of the cable itself – having a terminator installed (or enabled). It is important for devices between the ends of each cable to have their terminators removed (or disabled).
Here are some general guidelines for termination:
- Termination on internal SCSI peripherals usually is controlled by manually setting a jumper or a switch on the peripheral, or by physically removing or installing one or more resistor modules on the peripheral.
- Termination on external SCSI peripherals usually is controlled by installing or removing a SCSI terminator. On some external peripherals, termination is controlled by setting a switch on the back of the drive.
- By default, termination on SCSI host adapter card themselves is automatic.
- Internal Ultra2 peripherals are set at the factory with termination disabled and cannot be changed. Proper termination for internal Ultra2 peripherals is provided by the built-in terminator at the end of the Ultra2 internal SCSI cable.
- Most non Ultra2 SCSI peripherals come from the factory with termination enabled.