Online privacy is a growing concern in the United States and abroad. A 2014 poll showed that 61% of Americans wanted some variation of the European “Right to Be Forgotten” law.
People are even more concerned about the people that have control over their data. Polls from Pew Research showed that around half of Americans don’t trust either the federal government or social media sites with their data. As a result, a growing number of Americans and Internet users around the world are turning to VPNs to protect their privacy.
The New Perspective on VPNs and Online Privacy
In 2019, we became witnesses of global rethinking about online privacy. The result is clear: major consumers of social networks, online stores, and streaming platforms were forced to find solutions in order to keep their privacy on the Internet. Due to several privacy scandals, people prefer to hide their digital footprints. Most of them have chosen one of the options, mentioned at Vpn-review.com.

https://privacyinternational.org/sites/default/files/flysystem/2018-10/privacy%20%281%29.jpg
Global shifting
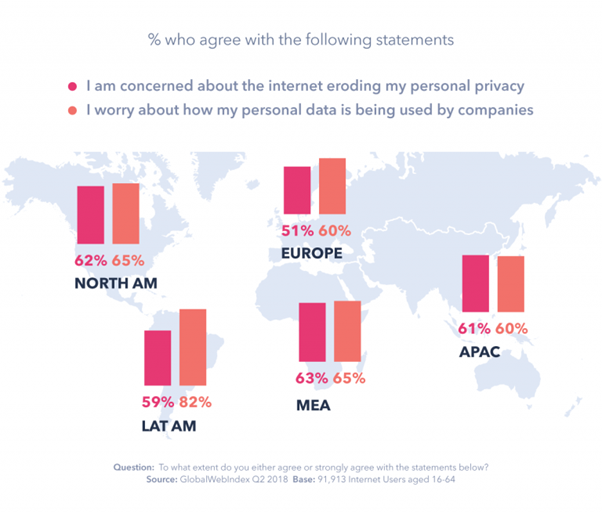
The research of the Global Web Index showed an increasing concern among the UK and U.S. Internet consumers over their online privacy (70%). It primarily means that companies working online should build trustful relations with their clients. First of all, it means the necessity to be compliant with new legislation as, for example, GDPR established in the EU. General Data Protection Regulation provides EU residents with tools for full control over their personal data. European users have the right to request confirmation of their data processing, the place, and purpose, the categories of personal data being processed, etc.
Lack of trust
Unfortunately, there are still a lot of countries in the world, where personal data is deliberately stolen and used by major companies or governments. It pursues more and more people to use VPN services in order to stay anonymous. For example, people from Latin America, the Middle East or the Asia Pacific regions are concerned about how companies use their personal info.
https://blog.globalwebindex.com/wp-content/uploads/2018/10/Data-and-Privacy-Blog-Chart-1-768×655.png
Therefore, the market for VPN services is still dominated by Asia and the Middle East. Here are Top-5 countries accessing content via VPN providers (According to Global Web Index):
1. Thailand (24% of users);
2. Indonesia (22%);
3. China (20%);
4. Brazil (19%);
5. Saudi Arabia (18%).
Most of those who use a VPN, do it at least once a week. Meanwhile, in the US or Germany the level of trust is much higher: 5% and 6% respectively.
The main reason to use VPN
Anonymity online is one of the main reasons for using a VPN, especially in Saudi Arabia, India, and Vietnam. Another reason to use it is online broadcasting. For example, almost 30% of all VPN users watch Netflix. But one of the most significant ones is the private information stolen. The fear of identity theft led to the fact that almost 30% of users in the United States refused to conduct financial transactions online.
When it comes to companies, the dangers and potential cybercrimes exceed their willingness to resist attacks. About 63% of companies do not have any procedures or action plans in this case.
Conclusion
With threats that are becoming more difficult day by day, the behavior of users on the Internet is changing. Major companies operating online have now to think how to pursue their customers to share private data. Until the approach in this sphere is still unchangeable, VPN keeps your anonymity in safe.
What do you think are the most up-to-date changes to be taken by the national governments? Do you trust your data to any online companies? Share your thoughts in comments.