Price Slicer may seem like a useful piece of software you can use to save money while shopping on the Internet. However, it is much more hassle than it is worth. They even tout the slogan of “Keep more money in your pocket with Price Slicer”. This is a piece of adware that will end up causing more problems in the long run. And, it will increase the likelihood that you will be further infected with other malware. In other words, you should remove it as soon as possible.

Price Slicer is developed to make money for its creators using the pay per click model. Basically, when you click on ads the developer gets money. Furthermore, it will record information about your surfing habits and the developers use this information to more finely tune their ads.
The software can also collect some private information like web log information and IP geolocation information. This information can be shared with third party advertisers as well which can open you up to further issues.
The ads you see can also redirect you to other websites that will unleash more malicious code onto your machine. This can be anything from more adware all the way up to harmful Trojan applications.
If you need an easy way to remove PriceSlicer from your system, we recommend SpyHunter. It is an easy, automated way to remove these types of issues from your computer.
Uninstall PriceSlicer from Windows.
- Open up control panel by clicking on the start button in the lower left corner of your computer, and then going to Control Panel
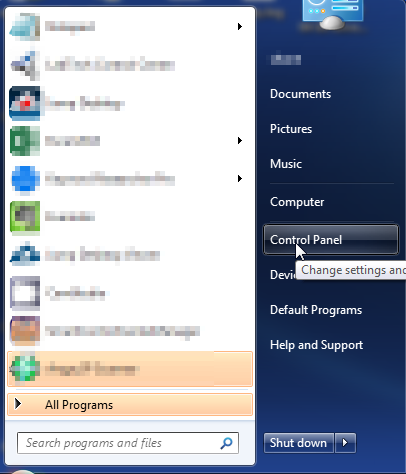
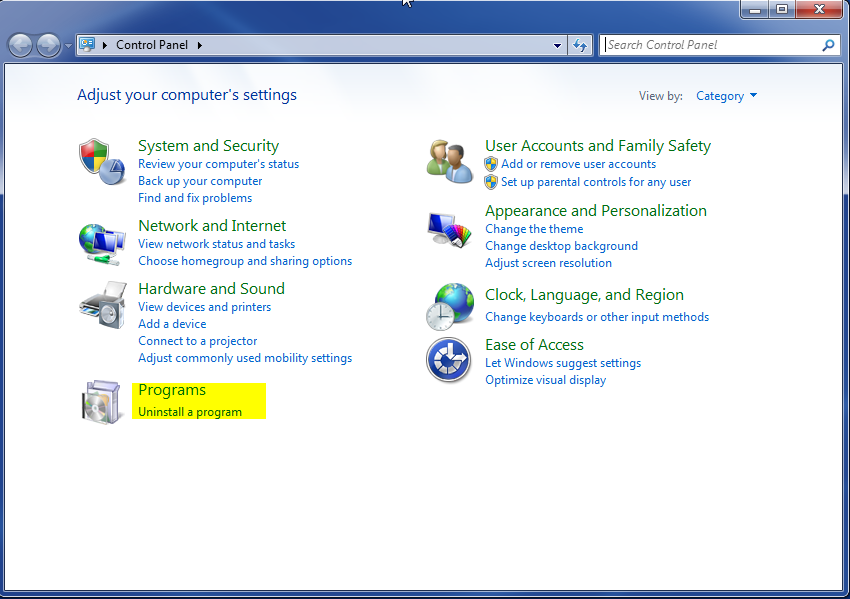
- Once, you are in Control Panel, go to the link labeled “Uninstall a Program”. If your computer does not look like the view below, you may have to sort by categories at the top right.
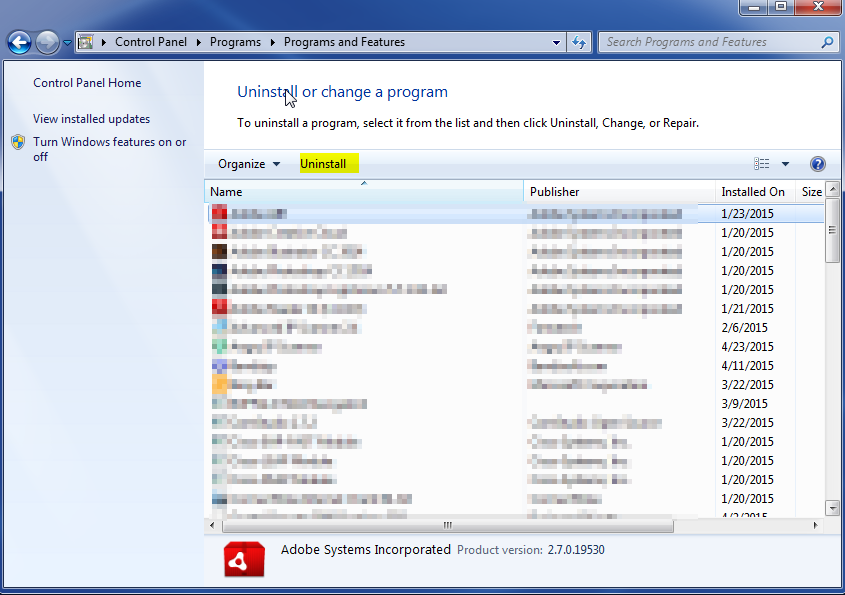
- Once in the uninstall programs section, look for the offending program. You can scroll by date installed to find programs that were installed recently. This may be a clue as to what the offending program is. Once you have found the program, highlight it and select “Uninstall” to remove
Once you have done this, you will need to go into your browser and set it to its default settings to remove the other changes it made. You will also want to scan your computer to make sure no new issues were introduced by the vulnerability. A good tool to use for this is MalwareBytes. If you already have a virus scanner, you should run this as well.
