In a previous post, I talked about enabling two factor authentication on your Google account. Just to rehash, two-factor authentication adds another layer of protection in your authentication method. You still login using your username and password. But, before you can go any further, a random number is generated and sent to a registered device. The device is typically a mobile phone. But, it can also be a specialty device that generates these numbers.
This means that even if someone guesses your password, they will still need access to your registered device to receive the special code. And, if they somehow get a special code one time it will change in a short amount of time. Two-factor authentication is so easy to set up that it really should be used when possible to add that extra layer of security to accounts.
You can read the previous post on how to enable two-factor authentication on the Google account. But, if you stop there you will receive your codes by text messaging. There is also an app you can install on your phone called the Google Authenticator App that will generate those codes for you. This is good if you do not want to pay for texts or if you would just rather have an app controlling this.
The first thing you need to do is to install the Google Authenticator App on your mobile device. You can go here to find the links for your appropriate device. Once you have installed the app on your phone, then you can proceed with the next steps.
Next you need to login to your Google account at https://accounts.google.com. Once you will scroll down to the area that says “Signing In” and click on the “2-Step Verification Section”
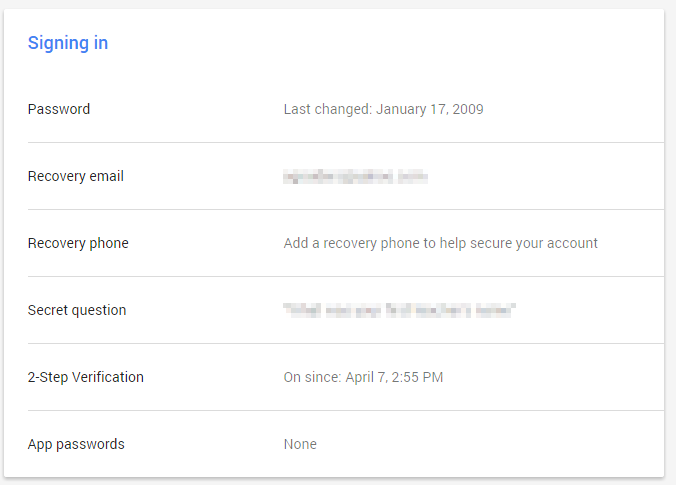
You will be taken to the next screen. As you will see the default when you enable 2-factor authentication is to use Text Message. To change to Google Authenticator App, you will need to click on the button that says “Switch to App”
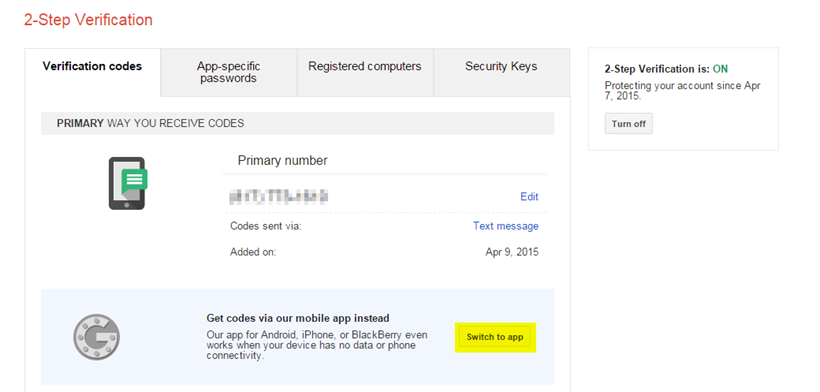
The next screen will have you pick your device type
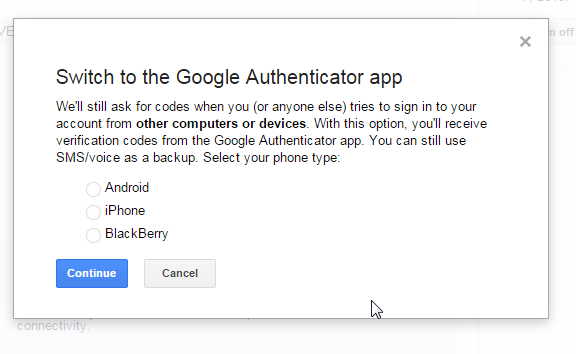
The next step will register your device with your account. You will get a screen with a barcode in the middle. This is what the screen will look like. But, you need to add an account to your app first
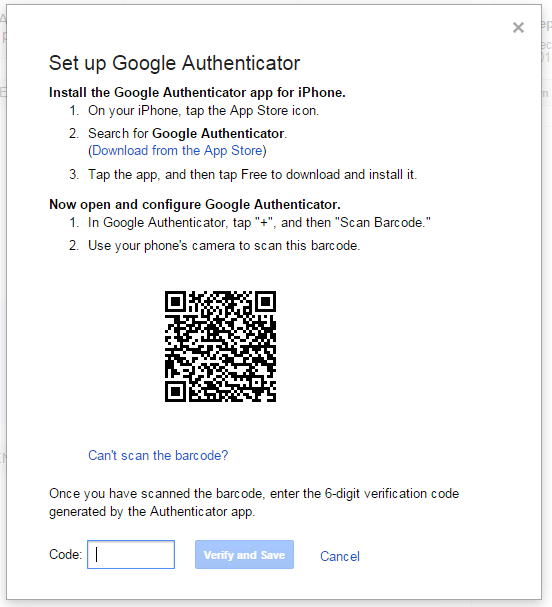
Open the app on your phone and click on the + sign to add an account
Click on the link that says “Scan Barcode”. It will open up a camera where you can hold it towards the barcode on your computer screen.
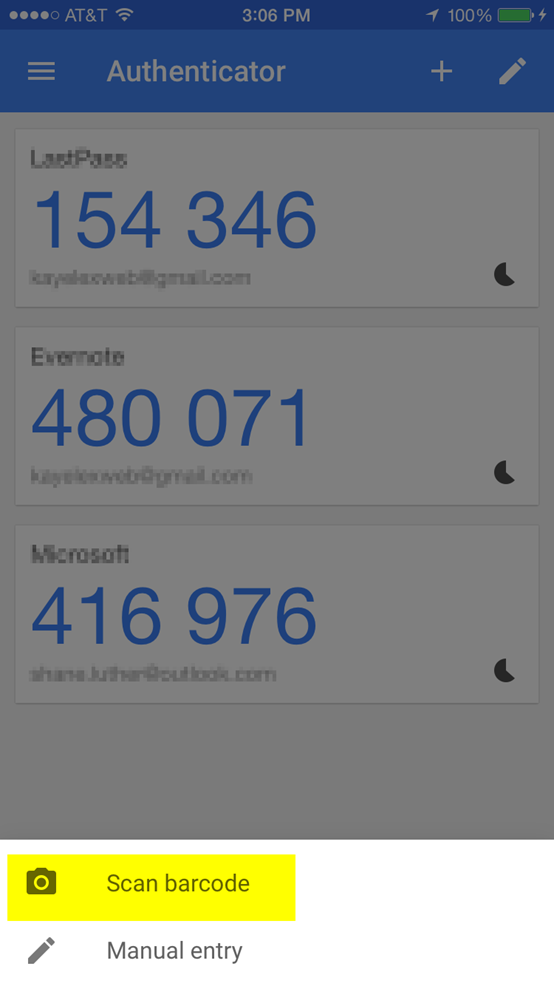
As you can see it has now added another entry for Google. This is the one you will use to login from now on
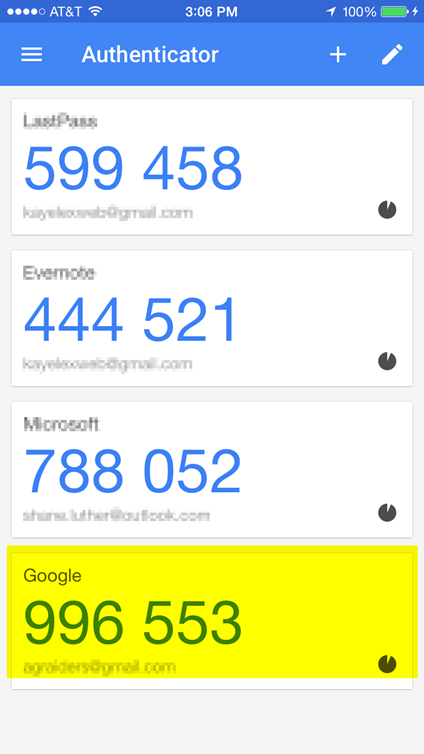
Your account is now set up to use the Google Authenticator App to login. From now on when you log into any Google property like Gmail, Calendar, Tasks, etc, you will use your username and password. But, it before going any further it will ask you for the 6-digit code on your phone inside the app. This code changes every 30 seconds on your phone as shown by the count down icon. If you do not enter the code in before the time expires, you will have to wait for a new number to be generated.