Intel’s Pentium Pro, which was launched at the end of 1995 with a CPU core consisting of 5.5 million transistors and 15.5 million transistors in the Level 2 cache, was initially aimed at the server and high-end workstation markets. It is a superscalar processor incorporating high-order processor features and is optimised for 32-bit operation. The Pentium Pro was also the first Intel microprocessor for some years not to use the venerable Socket 7 form factor, requiring the larger 242-pin Socket 8 interface and a new motherboard design.
The Pentium Pro differs from the Pentium in having an on-chip Level 2 cache of between 256KB and 1MB operating at the internal clock speed. The siting of the secondary cache on the chip, rather than on the motherboard, enables signals to get between the two on a 64-bit data path, rather than the 32-bit path of Pentium system buses. Their physical proximity also adds to the performance gain. The combination is so powerful that Intel claims 256KB of cache on the chip is equivalent to over 2MB of motherboard cache.
An even bigger factor in the Pentium Pro’s performance improvement is down to the combination of technologies known as dynamic execution. This includes branch prediction, data flow analysis and speculative execution. These combine to allow the processor to utilise otherwise wasted clock cycles, by making predictions about the program flow to execute instructions in advance.
The Pentium Pro was also the first processor in the x86 family to employ superpipelining, its pipeline comprising 14 stages, divided into three sections. The in-order front-end section, which handles the decoding and issuing of instructions, consists of eight stages. An out-of-order core, which executes the instructions, has three stages and the in-order retirement consists of a final three stages.
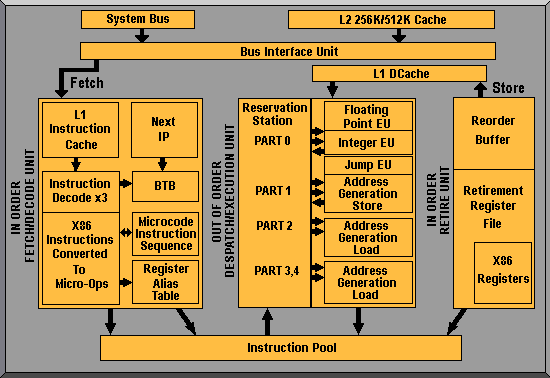
The other, more critical distinction of the Pentium Pro is its handling of instructions. It takes the Complex Instruction Set Computer (CISC) x86 instructions and converts them into internal Reduced Instruction Set Computer (RISC) micro-ops. The conversion is designed to help avoid some of the limitations inherent in the x86 instruction set, such as irregular instruction encoding and register-to-memory arithmetic operations. The micro-ops are then passed into an out-of-order execution engine that determines whether instructions are ready for execution; if not, they are shuffled around to prevent pipeline stalls.
There are drawbacks in using the RISC approach. The first is that converting instructions takes time, even if calculated in nano or micro seconds. As a result, the Pentium Pro inevitably takes a performance hit when processing instructions. A second drawback is that the out-of-order design can be particularly affected by 16-bit code, resulting in stalls. These tend to be caused by partial register updates that occur before full register reads and they can impose severe performance penalties of up to seven clock cycles.
The table below shows the various incarnations of the Pentium Pro processor from its launch in 1995:
| Date | Codename | Transistors | L2 Cache | Fabrication (µm) | Speed (MHz) |
|---|---|---|---|---|---|
| 1995 | P6 | 5,500,000 | 256/512KB | 0.50 | 150 |
| 1995 | P6 | 5,500,000 | 256/512KB | 0.35 | 160/180/200 |
| 1997 | P6 | 5,500,000 | 1MB | 0.35 | 200 |
- Pentium Architecture
- Pentium Pro
- Pentium MMX Technology
- Pentium II
- Pentium SEC
- Pentium “Deschutes
- Pentium Xeon
- Pentium III
- Pentium Tualatin
- Pentium 4
- Pentium Northwood
- Hyper-Threading Technology
- Pentium Prescott
- Pentium Processor Numbers
- Multi-Core Processors
- Pentium Smithfield
- Pentium D
- Pentium Roadmap