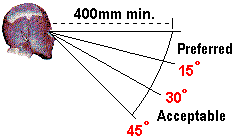
Whilst the quality of the monitor and graphics card, and in particular, the refresh rate at which the combination can operate is of crucial importance in ensuring that users spending long hours in front of a CRT monitor can do so in as much comfort as possible, it is not the only factor that should be considered. Physical positioning is also important, and expert advice has recently been revised in this area. Previously it had been thought that the centre of the monitor should be at eye level. It is now believed that to reduce fatigue as much as possible, the top of the screen should be at eye level, with the screen between 0 and 30 degrees below the horizontal and tilted slightly upwards. However, seeking to achieve this arrangement with furniture designed in accordance with the previous rules is not that easy to achieve, however, without causing other problems with respect to seating position and, for example, the comfortable positioning of keyboard and mouse. It is also important to sit directly in front of the monitor rather than to one side, and to locate the screen so as to avoid reflections and glare from external light sources.
- The Anatomy of a CRT Monitor (and CRT TVs)
- CRT Monitor Resolution and Refresh Rates (VSF)
- Monitor Interlacing
- What is the Dot Pitch of a Computer Monitor
- Dot Trio Monitors
- Grill Aperture Monitors
- Monitor Technologies: Slotted Mask
- Enhanced Dot Pitch Monitors
- Electron Beam Monitors
- Monitor Controls
- The Different Types of CRT Monitors – From ShortNeck to FST
- What is a Digital CRT Monitor and How Does It Work
- What is LightFrame Technology?
- Safety Standards For Computer Monitors
- TCO Monitor Standards
- Monitor Ergonomics