Perhaps emboldened by having attained technological leadership in the PC processor stakes with its seventh-generation Athlon chip, AMD announced its own vision of the path to 64-bit code and memory addressing support in October 1999 – and it was a lot different from Intel’s IA-64 architecture.
While IA-64 is a completely new architecture, AMD has elected to extend the existing x86 architecture to include 64-bit computing, adopting an approach that will provide an easy way for users to continue to use their existing 32-bit applications and to adopt 64-bit applications as needed. Fundamentally, the AMD x86-64 design – initially known by the codename Sledgehammer and branded as Hammer when the full architectural specification was released in mid-2000 – extends x86 to include a 64-bit mode that has both a 64-bit address space and a 64-bit data space – future 64-bit processors being able to detect which mode is needed and compute accordingly. The instruction set will be extended or operations such as instruction and data prefetching, with the only major architectural change expected to involve the x87 FPU.
AMD argues that its more conservation transition to 64-bit computing has a number of advantages over Intel’s IA-64 route:
- full native support for both 64-bit and 32-bit applications
- lower power consumption and therefore higher frequencies
- the potential for the fabrication multiple x86-64 processors on a single chip
- no reliance on complex new compiler technology
- less cost.
Its combination of support for both existing 32-bit x86 software with a true 64-bit x86-64 system architecture earns the AMD64 the right to claim to be the first eighth-generation x86 desktop processor architecture. The goal of delivering next-generation performance to the customer of today is achieved by striking a balance between next-generation microarchitectural per clock cycle performance and the ability to further scale the architecture in frequency in a given process technology.
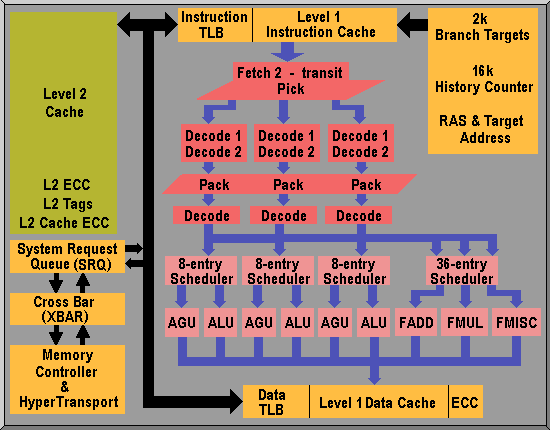
The changes to the Hammer’s base pipeline, as compared with the previous processor generation, are the clearest example of this design philosophy. The pipeline’s front-end instruction fetch and decode logic have been refined to deliver a greater degree of instruction packing from the decoders to the execution pipe schedulers. Accommodating this change requires a redefinition of the pipe stages in order to maintain a high degree of frequency scalability, resulting in two additional pipe stages when compared to the seventh generation microarchitecture. The end product is a 12-stage integer operation pipeline and a 17-stage floating point operation pipeline.
In the autumn of 2000 AMD released its SimNow! simulator – an application specifically designed to give BIOS vendors, tools developers, operating system manufacturers and application providers the ability to evaluate their x86-64 technology based software code prior to the release of its Hammer processors.
When AMD first announced their plans to extend their existing x86 architecture to include 64-bit computing, they were forecasting that this would happen before the end of 2001. In the event, problems with the adoption of SOI technology meant that it wasn’t until the spring of 2003 that we saw AMD’s K8 architecture evolve into the server-based Opteron line of CPUs. A few months later, the company was finally ready to launch 64-bit chips into the desktop and mobile markets.